Share Via
What has made Wi-Fi technology so pervasive and ubiquitous to connectivity is the fact that it operates in the unlicensed spectrum in the 2.4GHz, 5GHz, and the newly approved 6GHz frequency band. However, due to the unlicensed nature of the spectrum, it’s a double-edged blade. The proliferation of Wi-Fi products has introduced new threat vectors on the network landscape.
Wireless Sniffers and Snoopers
To begin with, anyone could sniff the wireless packets in the air medium using commercially available wireless sniffers and tools. Wi-Fi security protocols have evolved from WPA2 to harder-to-break WPA3 and introduced the enhanced Open security op-modes, which encrypt over the air communication between an access point and a Wi-Fi device. Still, there are other security vectors which threaten Wi-Fi communications. What are some of these other security threats?
Users are able to buy an off-the-shelf Wi-Fi access point and spin up a wireless local area network (WLAN), whether intentional or not. At a minimum these tools cause interference to other Wi-Fi networks in the vicinity. Furthermore, various off-the-shelf Wi-Fi simulation tools can inject Wi-Fi packets over the air causing interruptions to legitimate Wi-Fi connections.
Rogue Access Points (APs)
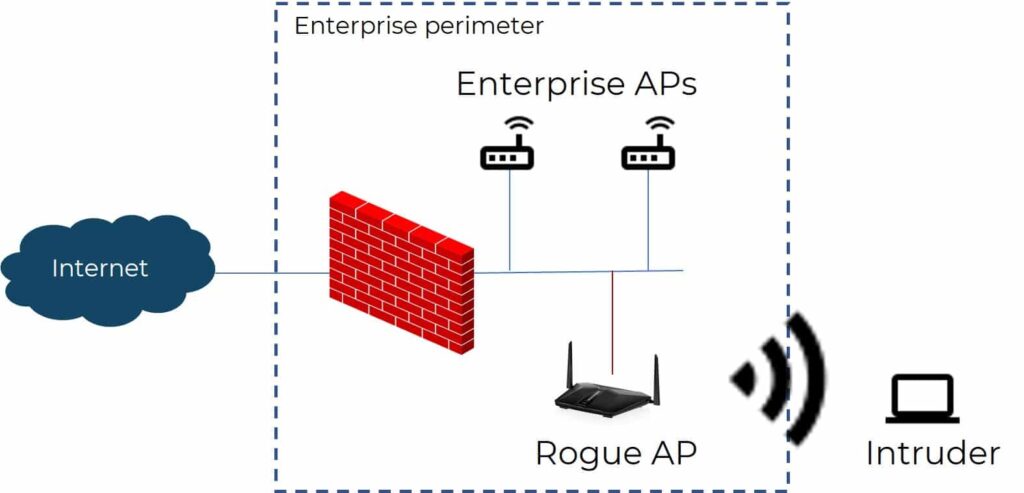
One of the top concerns for IT administrators and network managers of large networks is that an employee or inside bad-actor (using social engineering tactics) could connect an off the shelf Wi-Fi access point into the corporate wired network and broadcast its own WLAN to unsuspecting users. This creates an entry point for non-corporate devices to connect to the corporate WLAN and further into the network if thorough end-to-end security measures are not in place. This is a classic definition of a rogue AP. If not detected, bad actors can safely operate outside the physical perimeter of the enterprise, connecting to the rogue’s WLAN from the parking lot, finding an entry point into the enterprise LAN.
“The US Department of Justice charged hackers within the Russian military agency, GRU, with implementing evil twin access point (AP) attacks to pull sensitive data right out of the air[1].”
Honeypot or Evil Twin AP
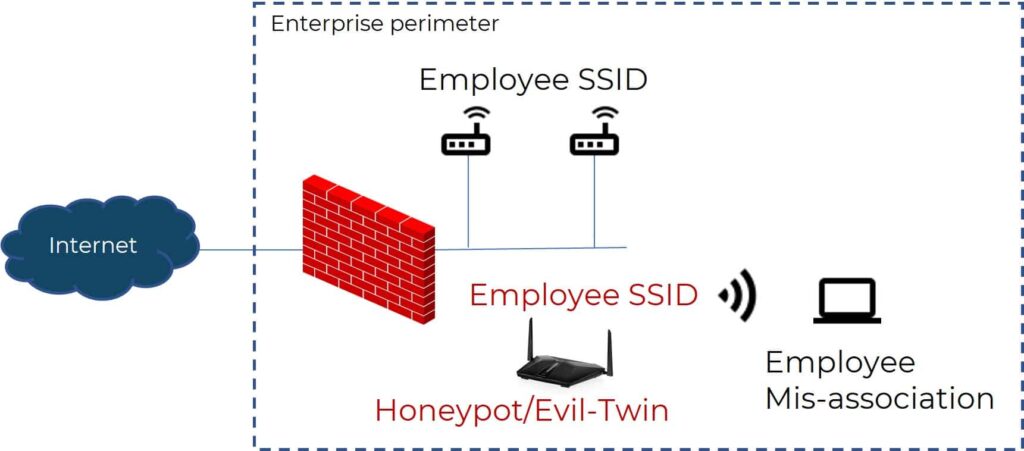
Another popular variation of the rogue AP is the honeypot or evil twin AP; in which a bad actor would spin up an AP that impersonates a legitimate enterprise AP’s network name (SSID) and/or the wireless mac address, to make it look similar. This impersonating AP acts like a man-in-the-middle to which unassuming guests or employees of that enterprise may accidentally connect. The MITM/honeypot AP could now redirect these user devices to an attacker’s local DNS servers and make them victims of phishing attacks.
“The team used the “evil twin” technique: create a new network and give the access point the same name as the true network, then record the credentials of a user attempting to log on[2].”
Nile Glossary: What Are WIDS and WIPS?
Get an in-depth look at wireless intrusion detection systems (WIDS) and wireless intrusion prevention systems (WIPS).
READ NOW
Additional Wireless Security Threats
In addition to the rogue AP and honeypot threats, there are other types of attacks possible over Wi-Fi. Denial of service (DoS) attacks that involve sending a flood of deauthentication messages to the connected devices, by posing as the access point, cause disruption to the end users. This type of attack could also be a precursor to the man-in-the-middle attempt, where an intruder tries to disconnect the connected devices from the legitimate access point first, in order to lure them to the rogue or honeypot AP.
There are several other types of DoS attacks possible using other types of management and control frames.
Wireless interferers that affect the Wi-Fi frequencies could be used by adversaries as a DoS tool by jamming certain frequencies.
Ad-hoc networks or peer-to-peer Wi-Fi networks, could be seen as a security threat by some network and IT managers. These typically involve a corporate-issued device connecting to another non-corporate network that may have been set up as a wireless Ad-hoc or peer-to-peer network by an adversary. Connecting to such a network could make it easy for malware to propagate into the corporate-issued device since its traffic is not going through the corporate network firewall.
“Those crooks can use this like a Wi-Fi jamming device, or a deauther, which can be the size of an Apple Watch[3]”
Enter WIPS and WIDS
These threats need Wi-Fi networks to employ thorough ‘intrusion detection’ and where possible ‘intrusion prevention’ systems. The terms wireless intrusion detection and intrusion prevention WIDS/WIPS stem from there.
Traditionally, the WIDS/WIPS enterprise WLAN vendor solutions have to be enabled and configured to provide the desired output of detecting lets say the rogue APs. The setup typically involves carefully classifying various types of devices seen in the vicinity. The settings for WIDS solutions can get fairly complicated. It requires an expert to tune the WIDS so it has the desired outcomes. Even after all these steps, that can run across tens of pages in user-guides, sub-optimal classification or errors can lead to more noise in the form of overwhelming number of alerts and notifications.
Nile NaaS Includes Extensive WIPS/WIDS
The Nile Access Service ensures that the overlay wireless security vector is secure. Traditional vendor-based WIDS solutions need a high level of expertise to configure the WIDS functionality. The complexity in these solutions requires experts to fine-tune the settings. If not done right, customers get an overwhelming number of events or alerts that could be false or inactionable.
Detect and block by default
Nile brings the ‘Nile way’ to WIDS by making it zero configuration, always on, and turnkey. The WIDS functionality kicks in right at service activation, taking on the onus to expertly enable the protection and alerting against top Wi-Fi intrusion threats.
Nile is able to effectively detect, alert, and mitigate rogue access points from the get go. The Nile WIDS uses sophisticated correlation techniques that intelligently filter out non-wired neighboring/friendly access points in the vicinity, to truly alert about real threats—such as a rogue access point that is connected to the LAN. The benefit of the Nile full wireless and wired LAN service is the end-to-end visibility. It is able to detect the port number where the rogue AP has been plugged in and block the port, thus stopping proliferation of the intruder into the wired LAN and further into the wider network. Furthermore, the rogue AP alert provides location information for the customer to send IT personnel to physically remove such rogue APs.
Staying ahead with cloud and analytics
Dedicated scan and monitor radios in Nile APs provide rich data about the wireless environment, which enables intelligent correlational detection algorithms that run in the cloud. This enables the Nile WIDS to run with holistic data from across all deployed APs at a floor, building, and site level. A WIDS solution designed with a cloud-first approach also means enhancements and updates to detect newer threats are seamlessly enabled for Nile customers, without needing a local system software upgrade!
Customer Example:
A healthcare customer with several clinics across the US, deployed Nile NaaS and found a wireless rogue AP connected to their network within minutes of activation. The customer was unaware that this rogue AP existed in their network. Most likely it was put in months ago to create a temporary network. This AP created security vulnerabilities by potentially creating entry points into their network from outside.
Extending WIDS capabilities
Nile WIDS is also equipped with effective detection and alerting for honeypot/evil twin APs that might be leading to an attempt at a man-in-the-middle attack. It detects an AP that could be impersonating a customer’s legitimate Nile access point SSID, wireless MAC address or both. There are other Wi-Fi threats possible as mentioned before. Nile WIDS has the ability to detect, alert and notify about these threats such as DoS floods using 802.11 deauthentication packets, presence of ad-hoc or peer-to-peer wireless connections, and wireless interferers. With intelligent classification of devices seen in the environment, Nile WIDS reduces or eliminates noisy false alerts, while clubbing that with more actionable alerting and notifications that include site and floor information.
Summary
At Nile, the WIDS functionality had to be re-imagined to blend into an as a service model. The complexity of configuring and tuning a sophisticated system like WIDS should be automated, simplified, and made actionable for the customers. Customers adopting NaaS should rest easy. The Nile Access Service protects them across various security vectors, including wireless overlay threats, which are still here and real!
Access these resources to learn more:
Share Via



