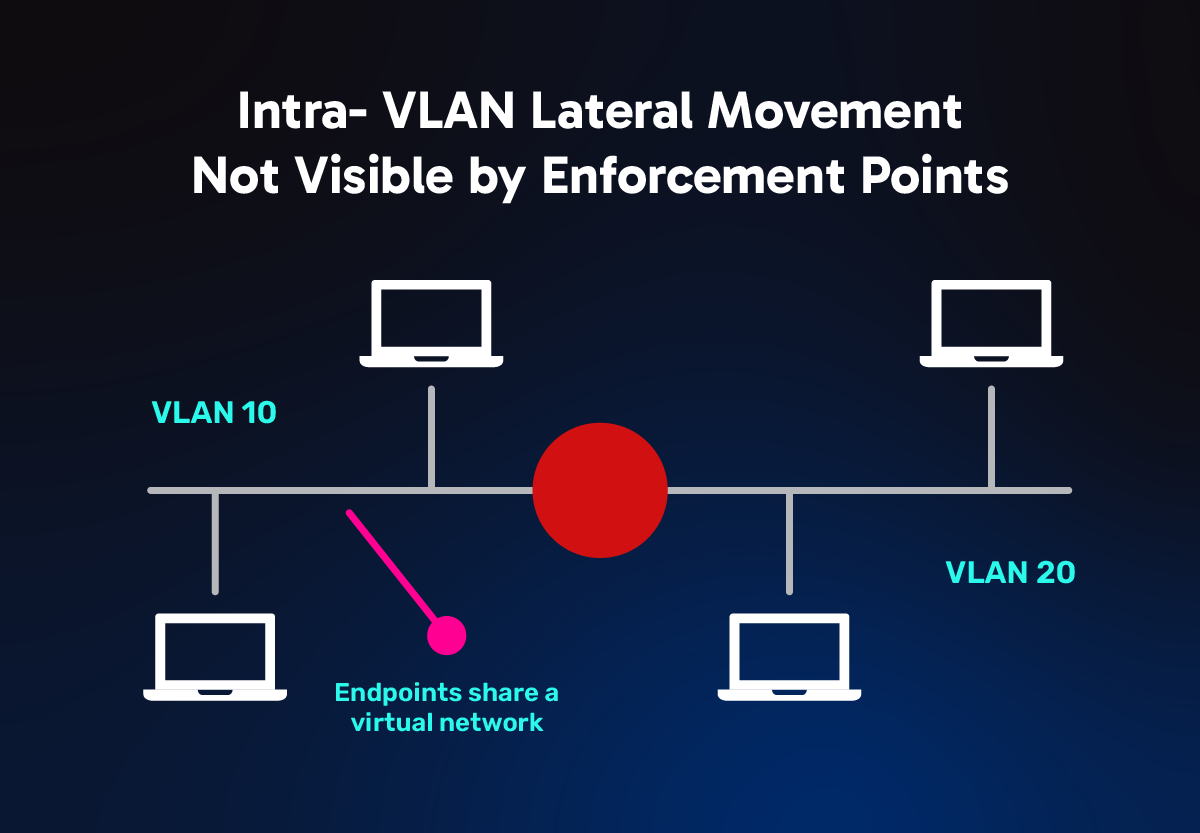
In a security context, lateral movement refers to a technique that enables an attacker to snoop on a VLAN or move through a network in search of data after gaining initial access. It involves techniques that enable a malware, ransomware, or other techniques to progressively move through a network, from one host to another.
These exploits often take advantage of VLAN vulnerabilities, misconfigurations, poor user behavior, and network architecture practices to obtain further access privileges and control. Lateral movement is typically used via internal and external cyberattacks, where the goal is to stay undetected for extended periods of time to maximize the ability to infect other devices, make them inoperable, or steal data.