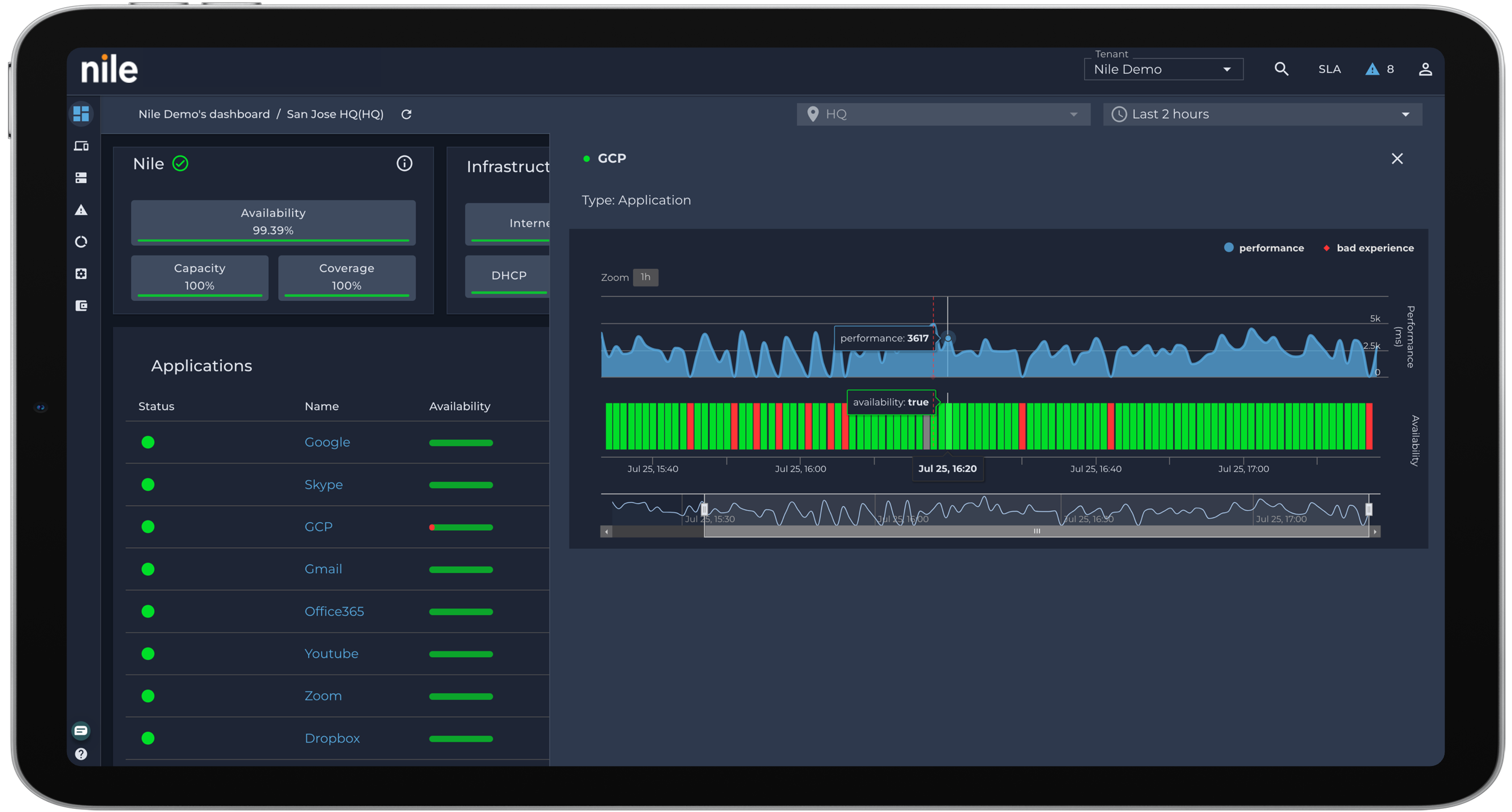
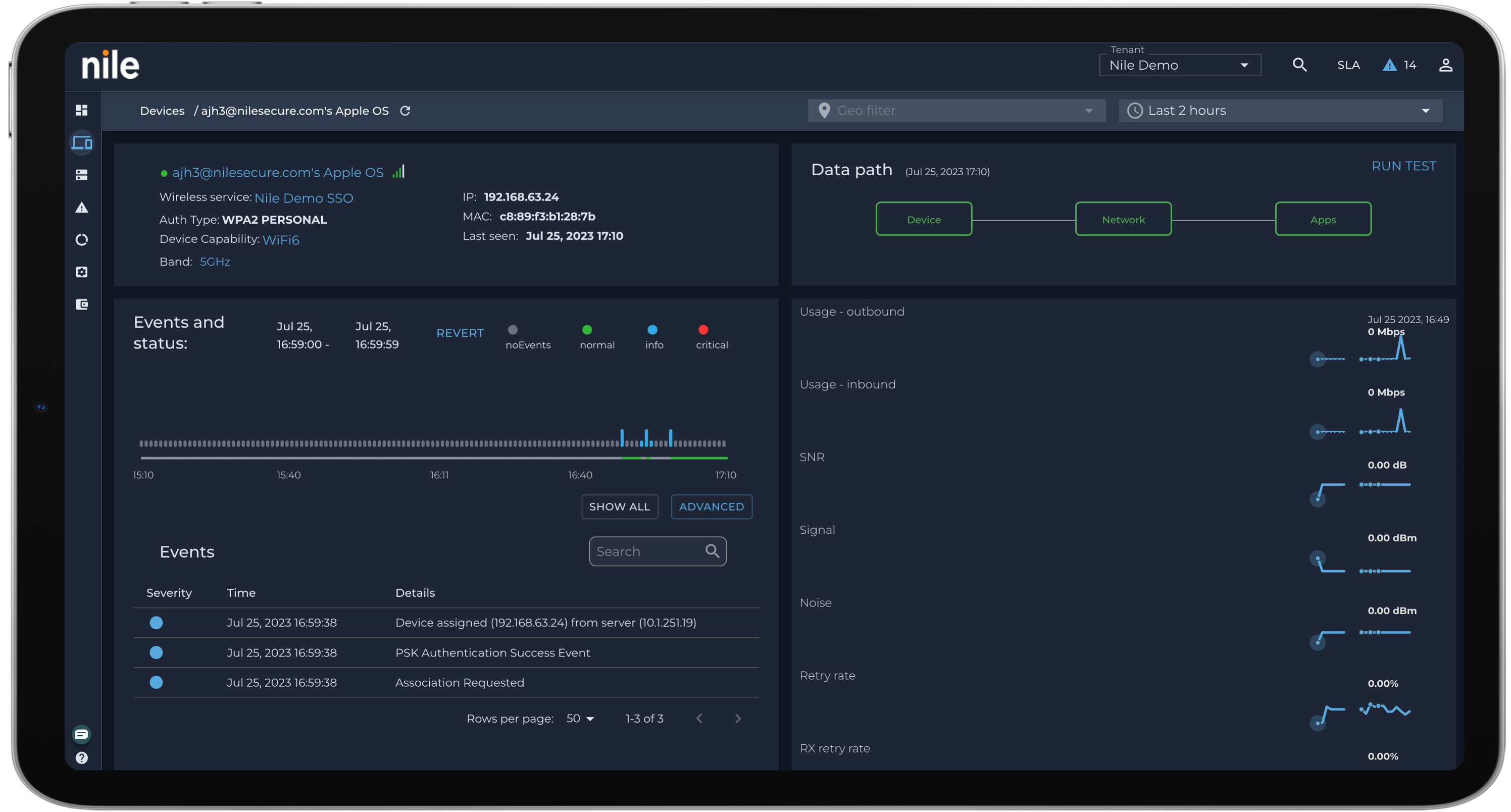
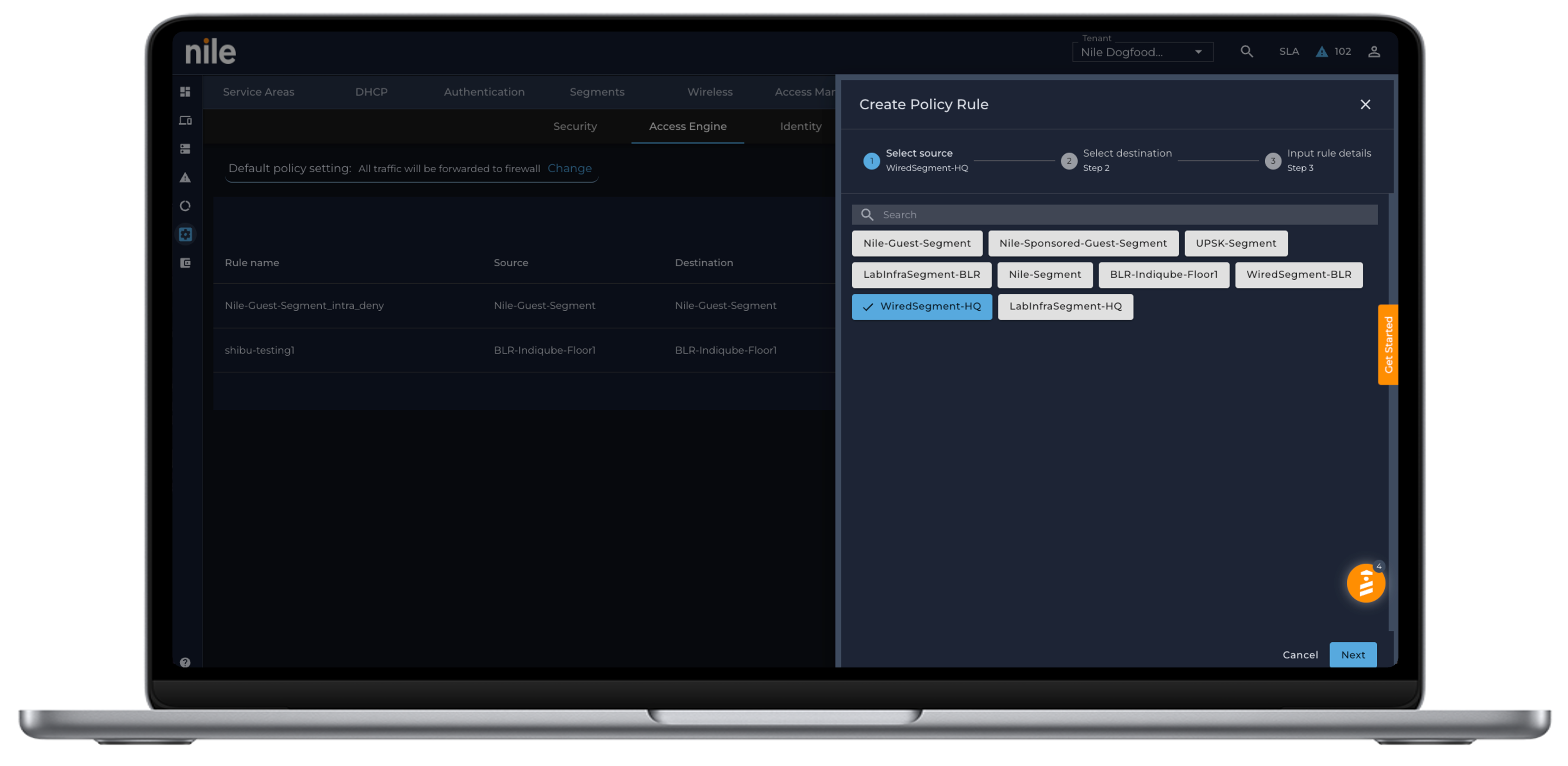
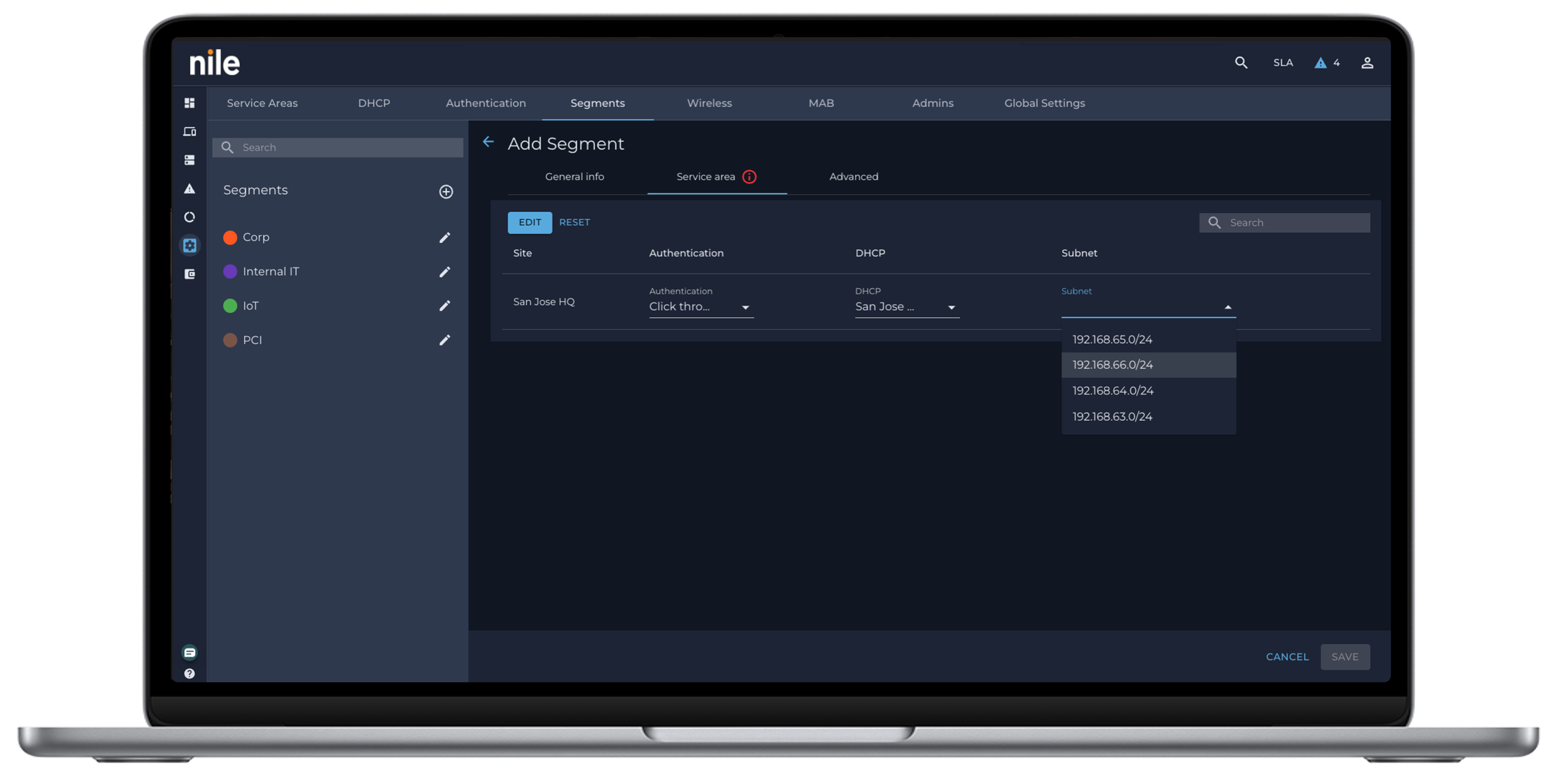
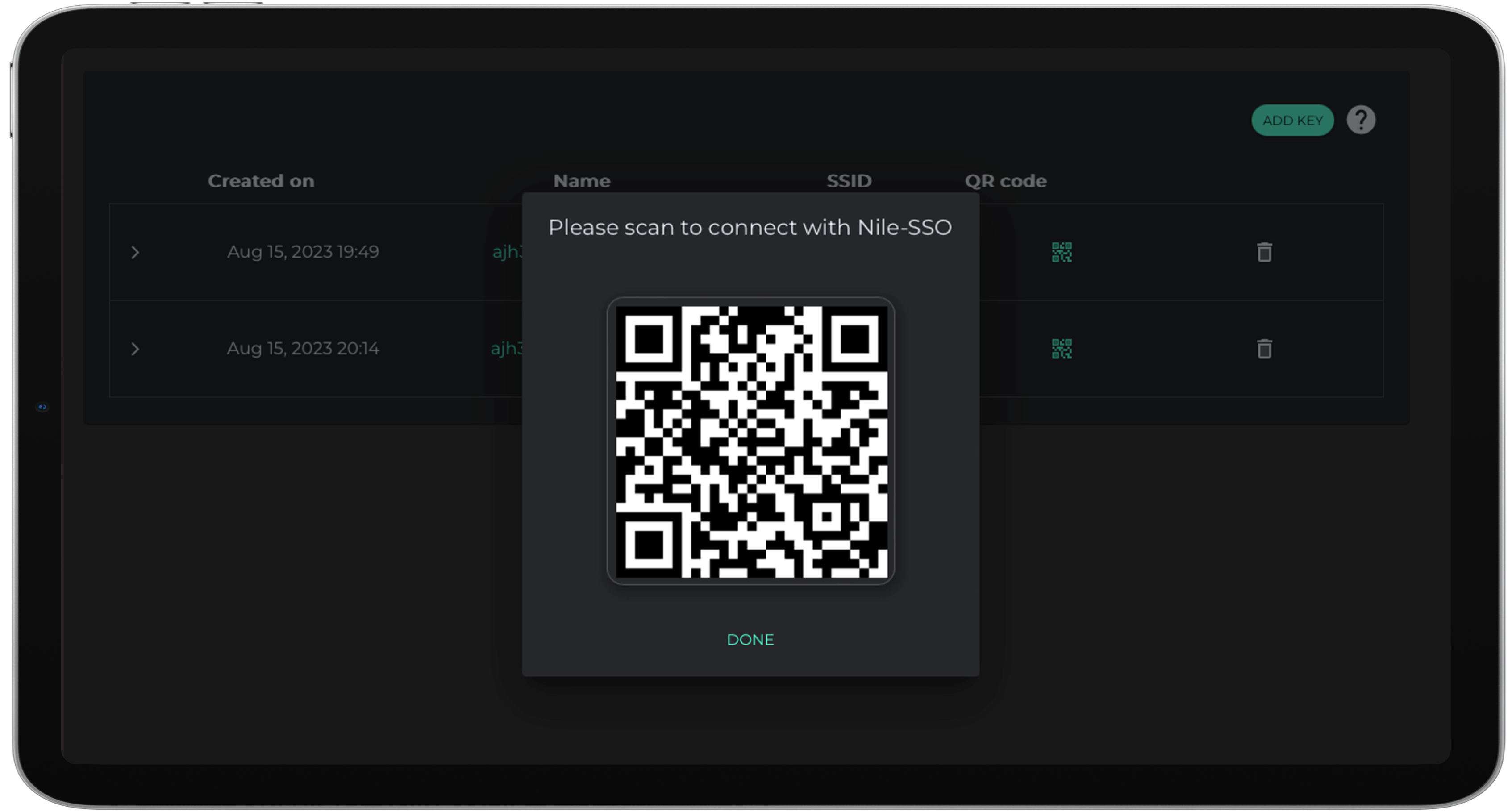
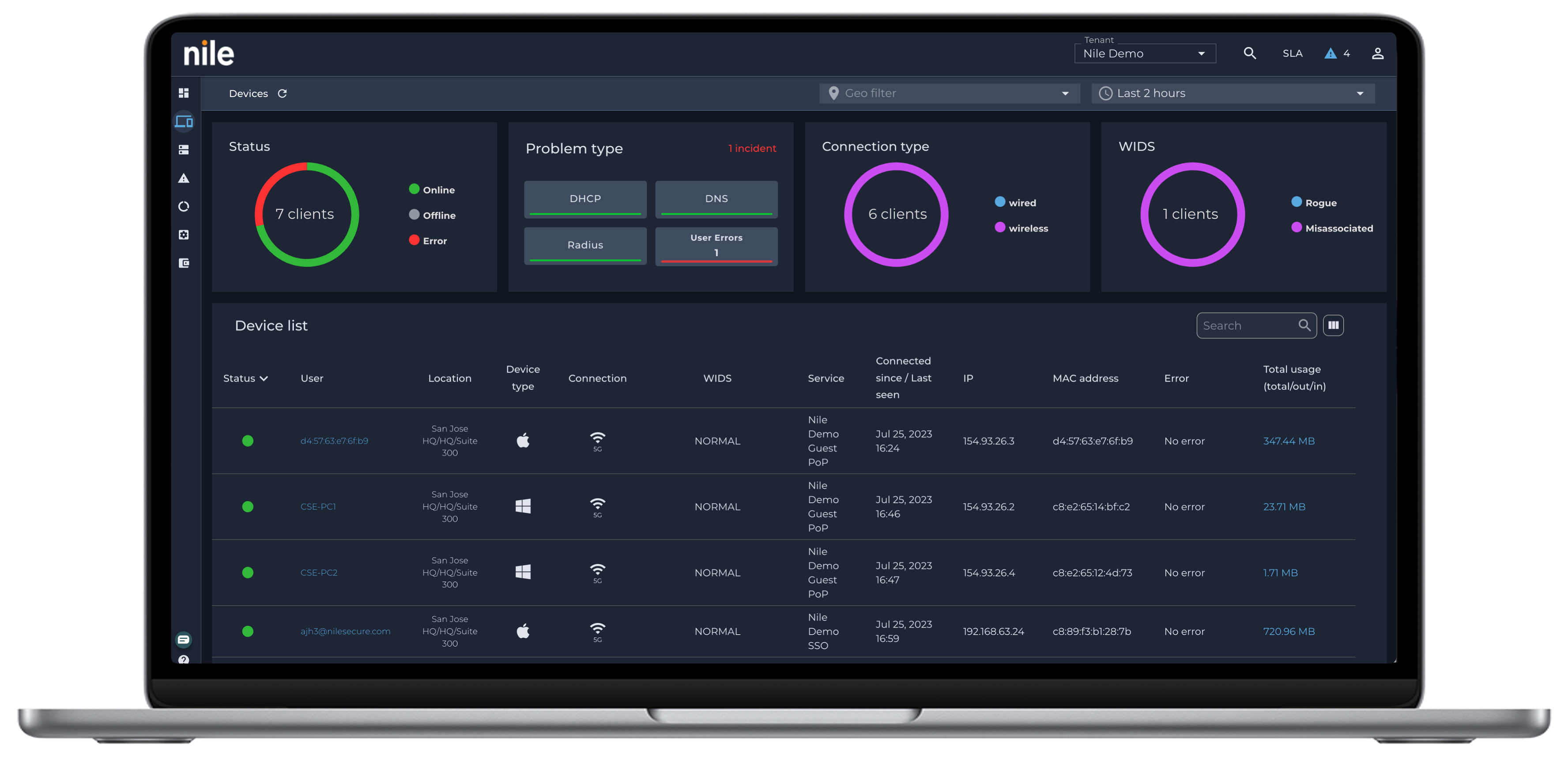
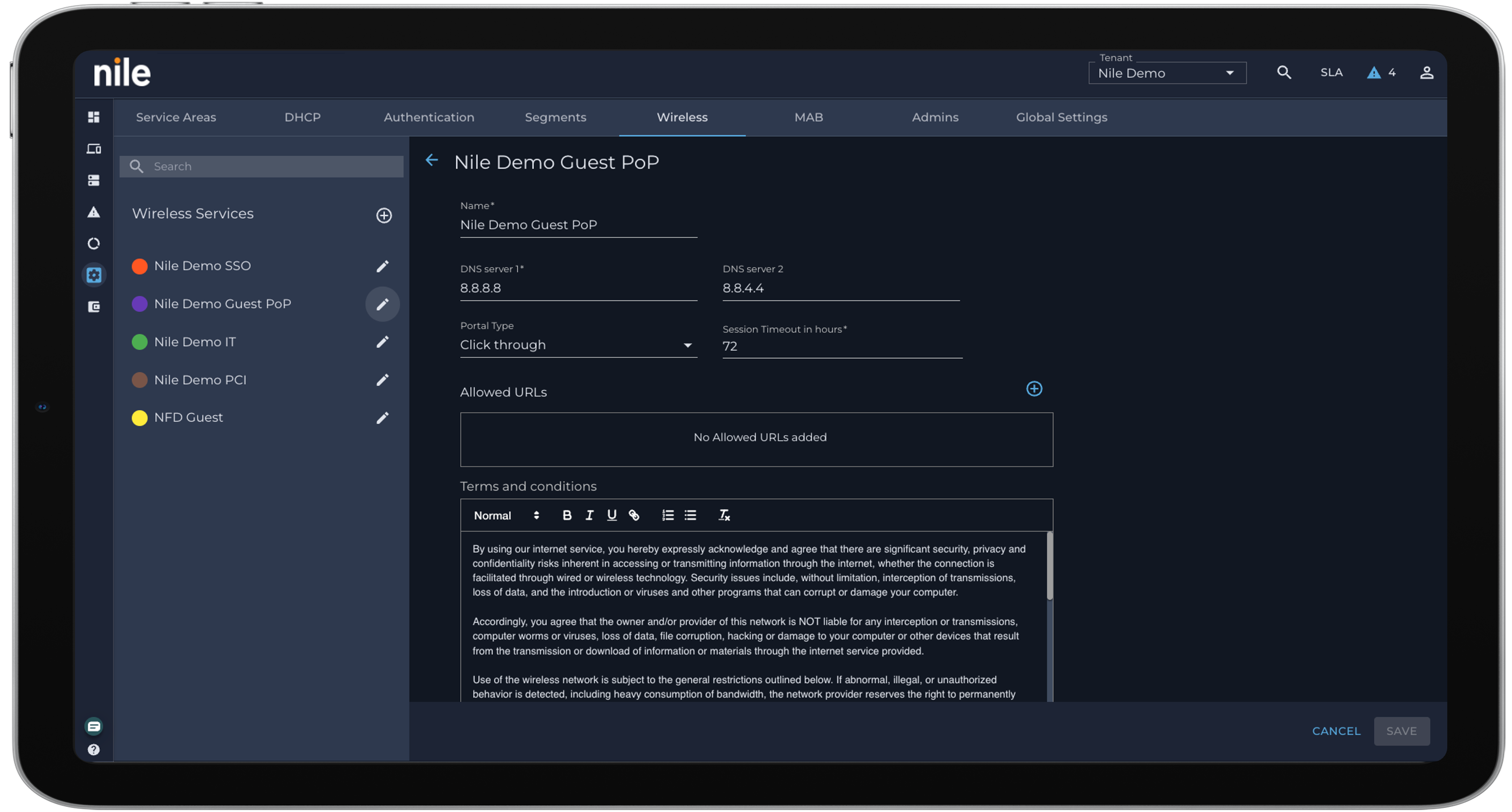
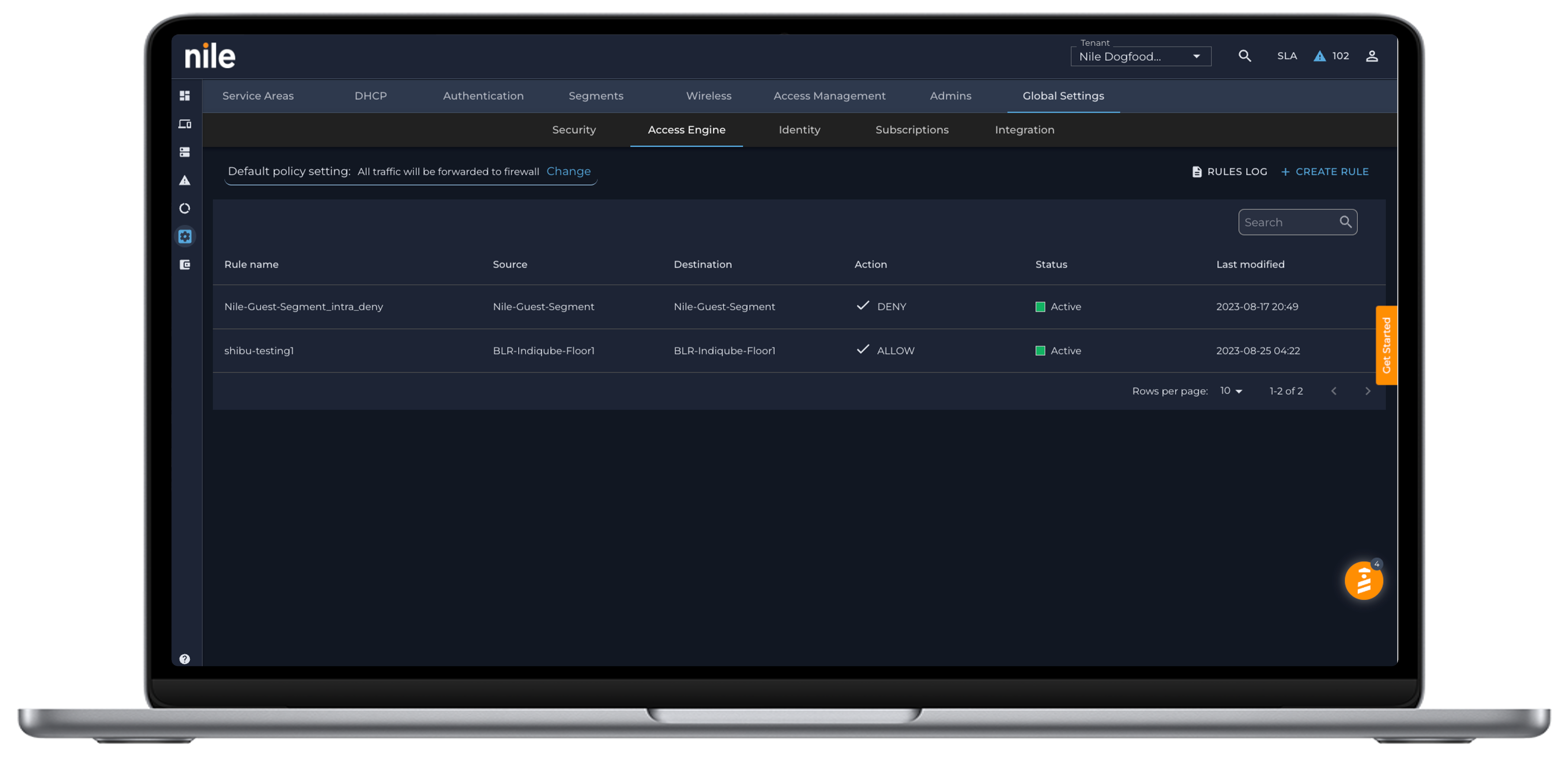
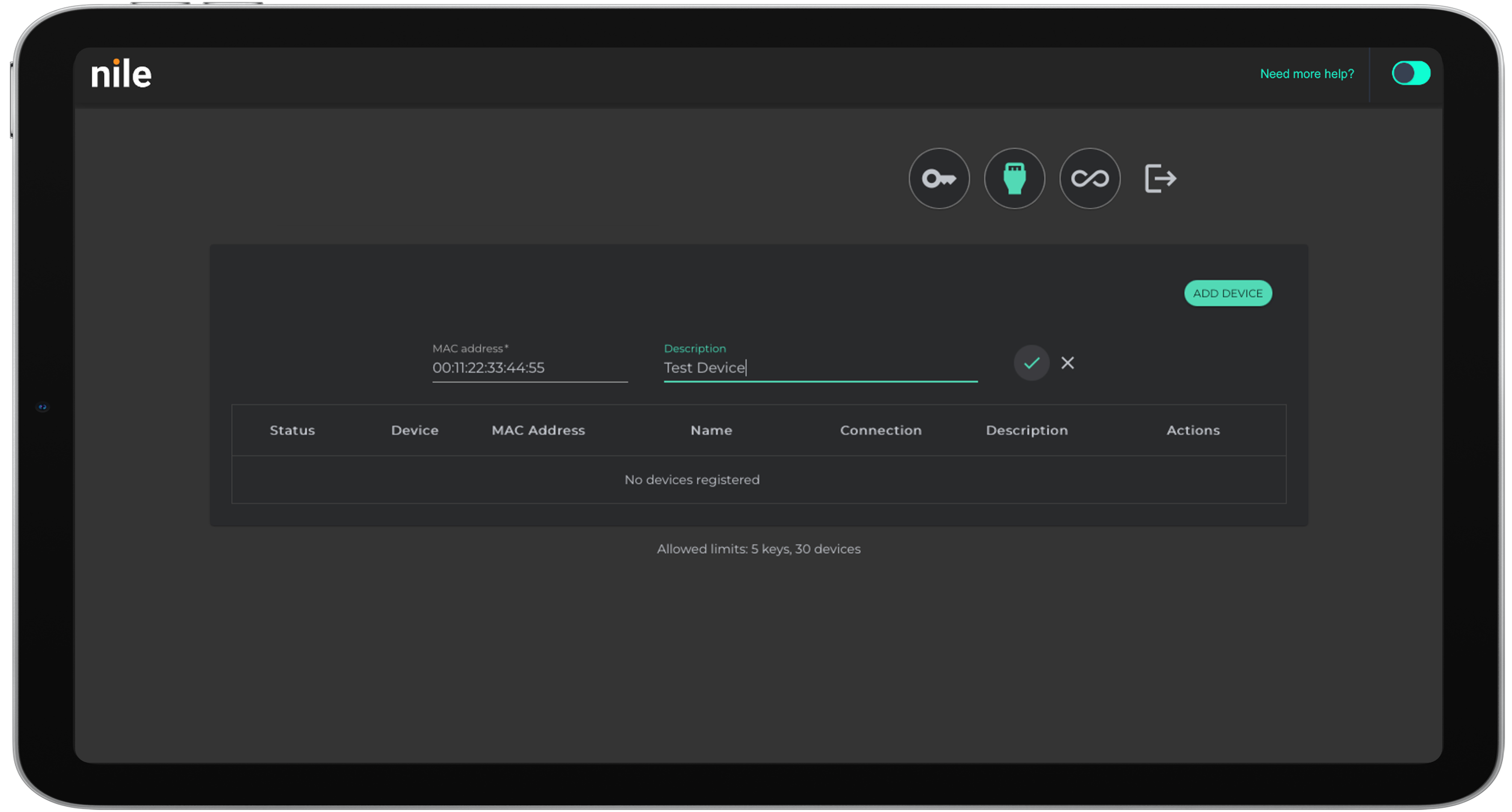
Ability to define granular network access privileges
IT teams face an ongoing challenge with defining proper network access privileges. BYOD and hybrid work users are especially vulnerable, creating openings for unauthorized access and potential attacks.