Simplicity Over Complexity
Authentication Without NAC Appliances
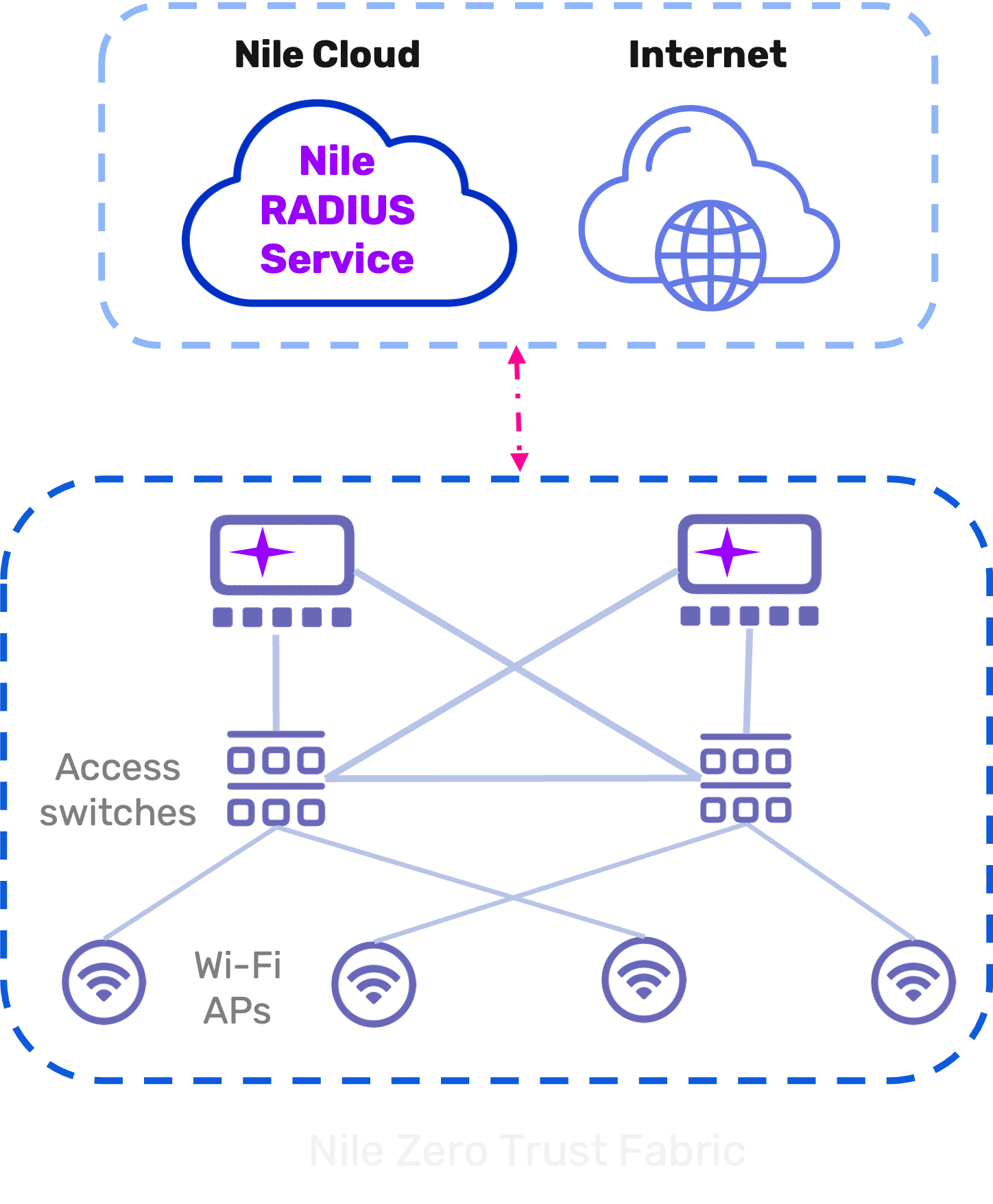
Once the Nile RADIUS Service is active, no manual tasks are required to begin. All transactions are secured automatically via gRPC tunnels. The sole configuration step is defining Policy rules. The Chaining of Policy rules even makes it easy to use existing identity stores or IdP and/or MDM solutions, and supports the following enhanced authentication requirement:
Rules based on Policy Chaining that include:
- Intune compliance
- SCIM for continuous authentication
- A restricted access policy, right out of the box
- RADIUS service monitoring
- Device authentication visibility for easy troubleshooting
Because the Nile Access Service and Nile RADIUS are vertically integrated, the “Restricted Policy” will automatically quarantine a device that is not recognized. With a redesign of outdated legacy principles, Nile eliminates the need for third-party integrations and the complexity that comes with them.