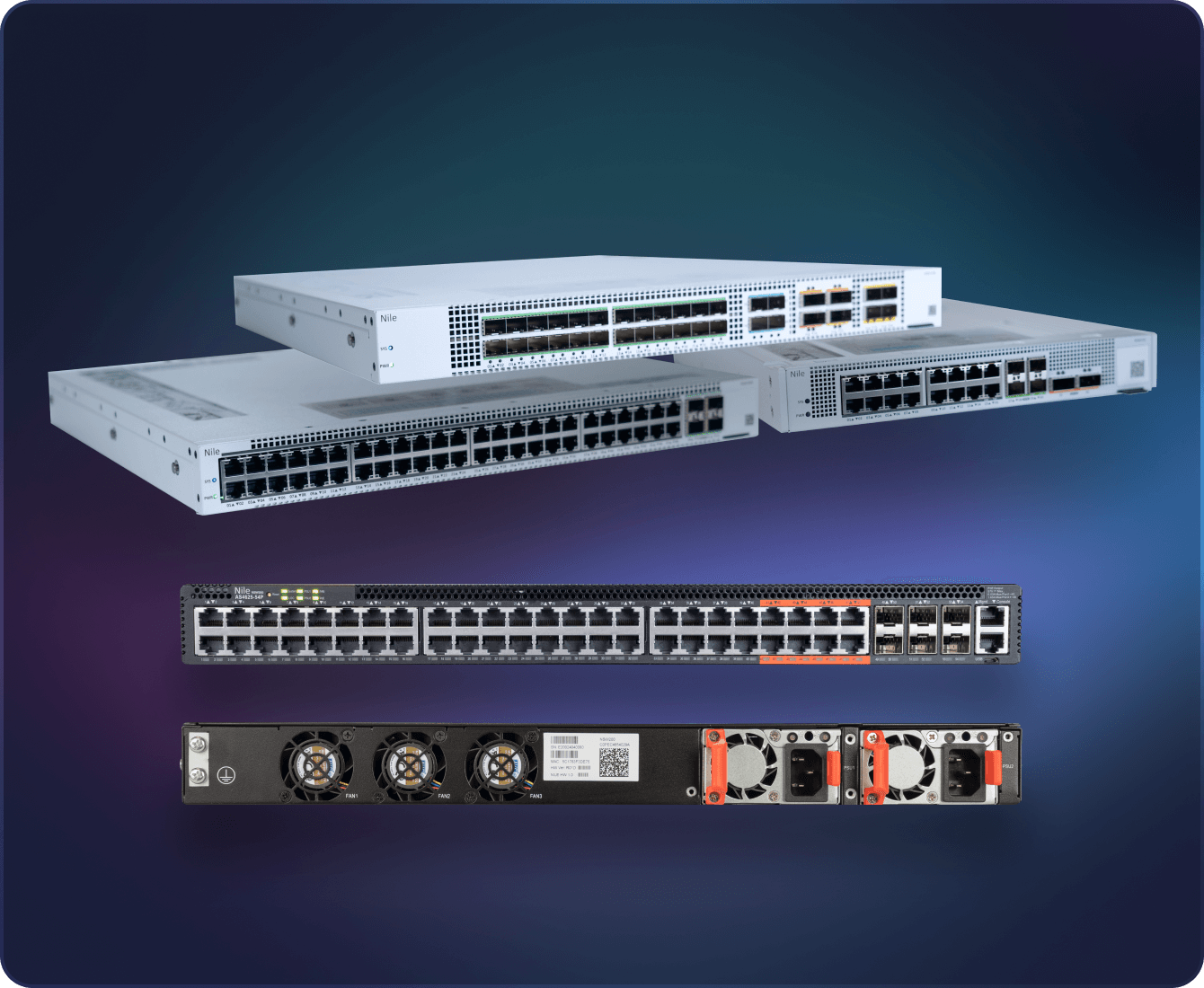
Nile Switches
Available in four different form factors to deliver wired and wireless connectivity to customers of any size. Nile switches are architected with high availability, tamper-proof design, Campus Zero Trust endpoint isolation, cloud management, and advanced AI automation features. Access switches include up to 48 MultiGigabit PoE+ ports, 4 10/25Gbps uplinks, and 2 100 Gbps ring ports. Distribution switches size up to 28 10/25 Gbps ports, 3 25/40/100 Gbps ports, and 3 40/100 QSFP ports. Most offer dual redundant load-sharing power supplies and hot-swappable fans.