Share Via
The ability for someone to wreak havoc on a business or organization is as easy as infiltrating a single device and using the weak spots in a network to explore. I’m often asked what I consider attack points or easy targets within a network, so I took the opportunity to share my cyber security experience with others at RSAC in San Francisco this year. It was a whirlwind trip with so many things to see and talk about.
As we all recover from the past week at RSA I’d like to discuss a pattern of attack vectors that many of my fellow security experts see exploited today. Numerous APT or criminal hacking organizations around the world are targeting equipment with limited visibility and stopping power. We’ve seen attackers avoid gear using EDR security, instead targeting IoT devices, network equipment, phones, and more.
Despite Hollywood’s depiction of a hacker slamming away at a keyboard, manually creating code to break systems, it’s not the reality. Often they are looking for persistence on devices and software that allow them to hide inside of your systems. Old and unpatched network switches are especially juicy. Once attackers are inside they will begin to explore. Some will passively and carefully listen to your broadcast traffic or aggressively scan and probe for open connections and known CVEs. The easy targets…
These devices are extremely vulnerable as technical debt and legacy practices do not really protect much and trust is not challenged or blocked. Since its inception, many networking protocols were written with implied trust. Unfortunately, there’s a skeleton in your network closet, which should chill you to the bone.
In an effort to help an evolving landscape of networking equipment get devices connected and working, a layer 2 broadcast domain that is chatty and trusting is used. Some infrastructure and tools provide limited visibility and worse, a very limited means to stopping an attack. In a worst case scenario where you can’t use software tools to stop an attack, you’re pulling cables and power as the industry famously observed during the MGM breach in 2023.
We must do better and evolve to modern switches that eliminate lateral movement, which is core to the problem. The biggest differentiator I see between old iron switches and a modern switch, like those from Nile, is the ability to break up the broadcast domain and provide visibility into what was previously a blind spot on your network. Let’s look at the differentiation.
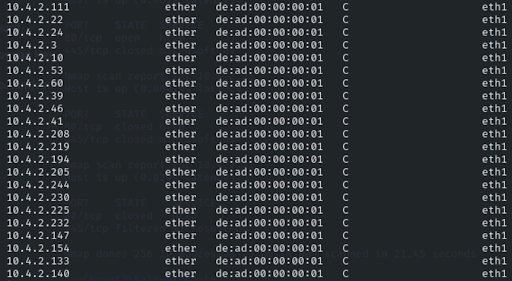
In this example we’re using nmap to do a port scan. The Nile switch responds back with the same bogus MAC address – DE:AD:1 – for every instance. Lateral discovery is prevented. In a switch from other vendors you’d see all of the devices real MAC addresses. That means that traffic can communicate directly over the switch without checking in with the firewall or your other security products.
Going further, the attempt is forwarded to the edge, in this case a Palo Alto Firewall which detects and drops the attempted port scan seen below.
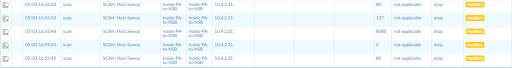
If a host is able to access another host on the same broadcast domain because a Nile policy has explicitly allowed the communication, all traffic is scanned by the firewall. Here we see a host attempt to send a malicious file, the Palo Alto firewall drops it. For the second packet we see a text file that was sent but not flagged as malicious and all is good. This is visibility that firewall and network teams gain into the backplane of a switching infrastructure they’ve never had before.
![]()
This is the space where the most lethal attacks happen and Nile is the only company that offers this level of security and visibility on every switch.
With purpose built zero trust switching hardware, you are able to isolate Layer 2 all the way to the interface. Filtered and challenged traffic is now managed with the individual use case in mind and your edge security is able to leverage real visibility and most importantly, stopping power in the Mitre attack framework.
This is a critical pillar in a secure network design and for the first time in decades, it’s available today. It’s a modern foundation of strength and a model that provides stability rather than a house of cards.


