Share Via
In today’s increasingly complex digital landscape, traditional security models have become obsolete. The rise of sophisticated cyber threats necessitates a more robust and proactive approach to safeguarding sensitive information. Constantly layering security solutions to fill gaps in campus infrastructure not only adds complexity but also struggles to keep up with evolving cyber threats, shifting business needs, and new technologies.
A new security model that challenges the conventional “castle and moat” mentality offers a compelling solution. By focusing on the connectivity of devices, their segmentation and continuous verification, as well as granular traffic inspection and enforcement, organizations can minimize the attack surface and bolster their security posture to protect critical assets. Campus Zero Trust cannot be a bolt-on security strategy – it has to be built-in.
In this blog, Shiv Mehra and I introduce the key principles of Nile’s comprehensive Campus Trust Service offering and how this translates to more efficient and effective enterprise-class security.
The Nile Trust Service
For decades, traditional security models have relied on perimeter defense mechanisms to secure network boundaries. This approach has proven inadequate in the face of remote access, hybrid work, and advanced cyberattacks that bypass external and internal defenses. As threats evolve, so too must our security strategies. A paradigm shift in how cybersecurity is built into a network offers a more effective and resilient approach.
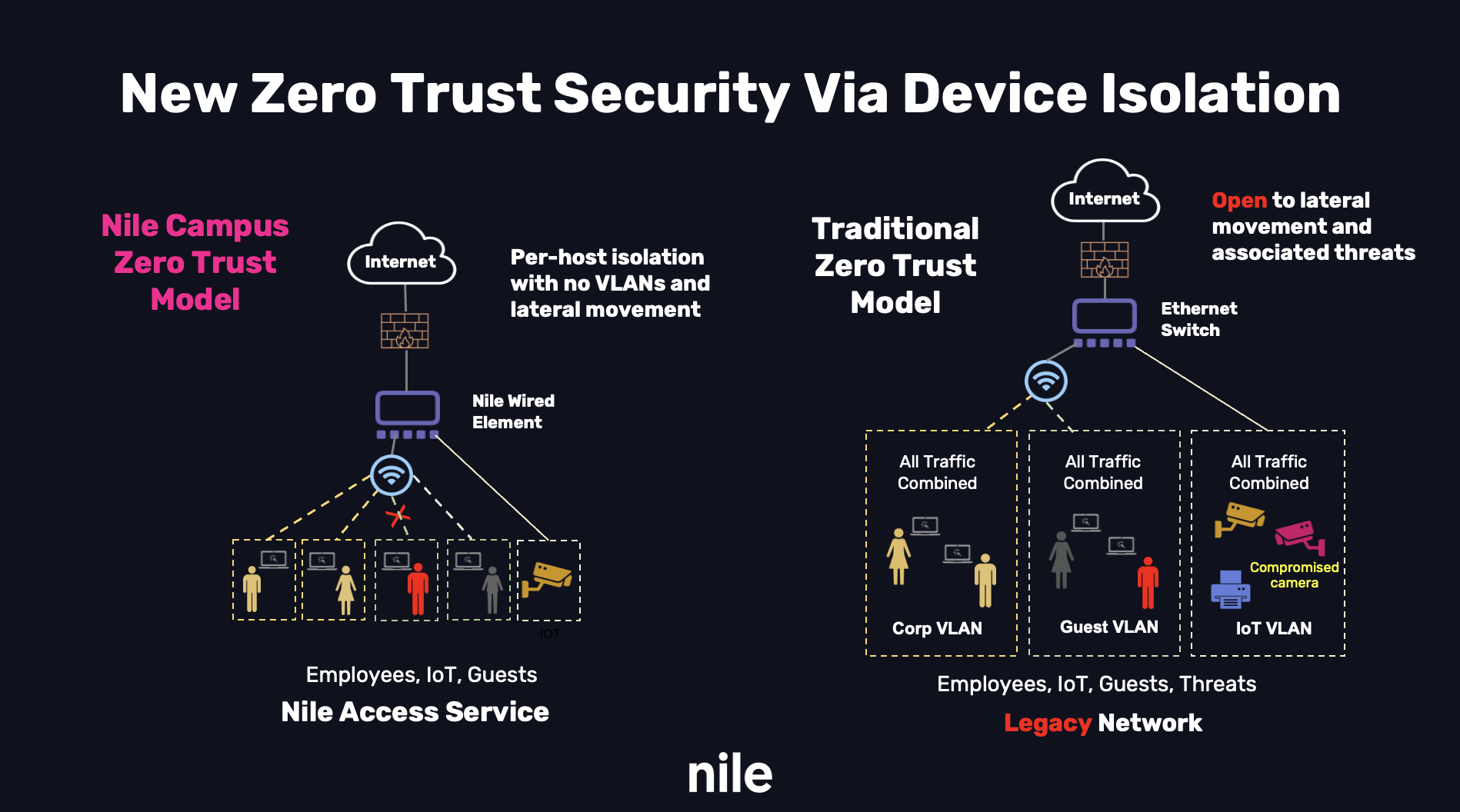
To help fill today’s campus LAN security holes, we’ve built modern campus zero trust principles into the Nile network that is delivered via built-in Nile Trust Service security at every layer. By stepping back and taking a ground-up approach, gone are inherent weaknesses such as VLANs, lateral movement within and across VLANs, complex access control lists, and the silos that come with bolting on and managing disparate point solutions.
The image below compares the Nile implementation versus the traditional model and highlights basic weaknesses that are still in use today by others.
The Core Principles of Nile’s Trust Service
At the heart of this new Campus Zero Trust approach lies a fundamental principle: never trust, always verify, and for the first time, start with the isolation of each and every connecting device. This means that each user, device, and application, regardless of its origin or location, is considered potentially hostile until proven otherwise. By implicitly adding a much-needed layer of isolation, this new Campus Zero Trust model significantly reduces the attack surface and minimizes the potential impact of successful breaches.
The keys to the new Nile Trust Service framework:
1. Campus Zero Trust Infrastructure:
- Per-device Isolation: Each user and device is placed into a “segment of one” to limit the impact of a compromise and its blast radius to that specific device.
- Hardened Infrastructure: The removal of weak links that allow traditional infrastructure to be compromised via console ports, shared passwords, and malicious insider threats.
- Encrypted Communication: The protection of sensitive data by encrypting all communication within a Nile Access Service deployment – from the network infrastructure itself to each connected device.
- Up-to-Date Software: Automatic updates ensure the latest and greatest security patches and features provide our customers a secure and stable environment.
2. Campus Zero Trust Access:
- Strict Controls: Enforces precise limits on who and what can access specific resources. IT teams gain robust access control that includes support for basic authentication, single sign-on (SSO), multi-factor authentication (MFA), and strong password policies.
- Continuous Authentication: The verification of the identity of users and devices to ensure proper authorization privileges. This ongoing process helps to detect and mitigate potential threats.
- SCIM Support: Built-in System for Cross-domain Identity Management (SCIM) provides the ability to treat network access like an application, thus leveraging onboarding and denial of access systematically.
3. Campus Zero Trust Policy:
- Unified Enforcement: Customers gain the ability to apply consistent security policies across remote and on-campus users/devices. Built-in Secure Service Edge (SSE) support with Zscaler, Palo Alto Networks and Microsoft allows for a universal model where even IoT devices are protected by the same corporate security levels defined for laptops and phones.
- Least Privilege Access: Due to the large use of Wi-Fi today, organizations can easily minimize the risk of unauthorized access by granting users and devices only the necessary permissions to perform their tasks. With Nile’s segment of one approach and the ability to define simple group and user based rules without complex NAC integration, organizations of all sizes can create comprehensive policies that are easy to implement and adjust.
- Contextual Data Protection: A unique safeguard to protect sensitive data by applying deeper policy controls based on user identity, device context, and a sensitivity rating. The idea is to leverage “Trust Levels” based on authentication type, corporate or personal device ownership, security posture, and/or connectivity type (wired or wireless). We’re making it easy for the networking admin to apply security controls for a device authenticating based on SSO, CrowdStrike device security posture assessments, or access based on day-of-week to protect sensitive data and stop breaches.
Benefits of Shifting to a Nile Trust Service Network
By adopting Nile’s new Campus Zero Trust security model, we’re providing organizations with numerous benefits that include:
- Enhanced Security: A significant reduction in their overall attack surface that limits the potential impact of targeted breaches. Simple and smart access control features eliminate implicit trust, allowing organizations to better protect their sensitive data and critical infrastructure.
- Improved Resilience: Organizations can identify and contain internal and external threats more quickly. The isolation of compromised systems and limiting the spread of attacks help minimize downtime and financial losses.
- Increased Compliance: An improved security foundation that begins with a secure Campus Zero Trust architecture enables organizations to meet various industry regulations, including GDPR, HIPAA, and PCI DSS. The implementation of strong access controls and monitoring of user activity allows organizations to demonstrate their commitment to data protection.
- A Superior User Experience: While some Campus Zero Trust features seem restrictive, they can actually improve the user experience by offering consistency, regardless of where they are connecting from. By automating many security tasks and streamlining access processes, organizations can reduce user friction as they connect everything from a laptop to an IoT device, thus increasing productivity.
Conclusion
Amid an evolving digital threat landscape, the Nile Trust Service implementation offers a powerful and effective approach to cybersecurity. By challenging traditional assumptions and prioritizing continuous verification, Nile is empowering organizations to build a more resilient and secure network without complexity that supports any future technology and workplace demands.
By adopting this paradigm shift, organizations can easily protect their critical assets, mitigate risks, and ensure the confidentiality, integrity, and availability of their data. The campus is no longer your weakest link.