Share Via
Accessing the Internet and cloud resources via Wi-Fi from various locations has become an integral part of our lives. Whether visiting a business, hotel, airport, or elsewhere, connecting to a guest wireless network is something people instinctively do today. Unfortunately, convenience often outweighs concerns about the security of our devices and data, as well as the data and resources that belong to our employers or organizations.
While public Wi-Fi hotspots and enterprise guest networks are readily available, most are anything but secure. Mainstream wireless solutions continue to use VLANs that place everyone’s devices onto a shared domain that allows for lateral movement, threats and loss of data. This realization has crossed our minds here at Nile and led us to build basic zero trust requirements into our Nile Access Service. Security should be built into the foundation of your network when offering guest access to visitors, shoppers, and passengers or you provide a point of access that can be easily compromised.
The following are some key points to consider when offering a guest network today:
- Ease of Use: The primary expectation when connecting to a guest network is that it should “just work.” Guests, visitors, shoppers, etc., expect a seamless experience where they can quickly connect, send emails, access files, and browse the web without any hassle. Nile has made it simple for users and you’re not required to add an external NAC solution or captive portal as these features are built into our solution to remove complexity.
- Network Design and Security: The security of guest networks today varies widely. Most vendors offer minimal security measures, potentially exposing users’ devices to threats such as snooping and eavesdropping. While some guest networks may be secured with additional encryption protocols, this is rare as it adds IT and user complexity that hampers the experience. Nile is the only solution that provides per-host isolation and encryption on day one that extends from your internal network to your guest SSID. No complexity.
- Data Protection: When using a traditional guest network solution, data is vulnerable to interception by malicious actors who are also connected to the guest VLAN. This is especially risky when transmitting sensitive information such as contracts, personal information, or engineering documents. It is not safe to assume that simple segmentation based on VLANs will suffice. Legacy practices such as requiring VPN clients are also not effective and add complexity that impacts ease of use. Let’s look at two scenarios:
- Many organizations ask their employees to use VPNs (Virtual Private Networks) for extra protection when using a guest network to encrypt traffic and ensure their data remains private, but this is often overlooked and is not completely enforceable.
- Personal devices are at greater risk as using VPNs is not a common practice among the general public.
To address these needs, Nile has completely redesigned its architecture to isolate every wired and wireless device that connects to a Nile network. We’ve eliminated VLANs and all traffic is isolated via layer 3 segmentation, thus making lateral movement between devices impossible. In most cases each device is tunneled to a firewall, inspected, and only allowed to reach predetermined destinations, typically the Internet for guest users.
The Nile Architecture Difference
It’s important to understand how Nile differs from other vendors in regards to VLANs and segmentation. The following diagram highlights how a traditional VLAN-centric network is structured and how a malicious actor can take advantage. Once connected to a guest Wi-Fi network, bad actors have the ability to view and manipulate devices and data within that VLAN and will often look for any holes between VLANs that allow for lateral movement across the organization.
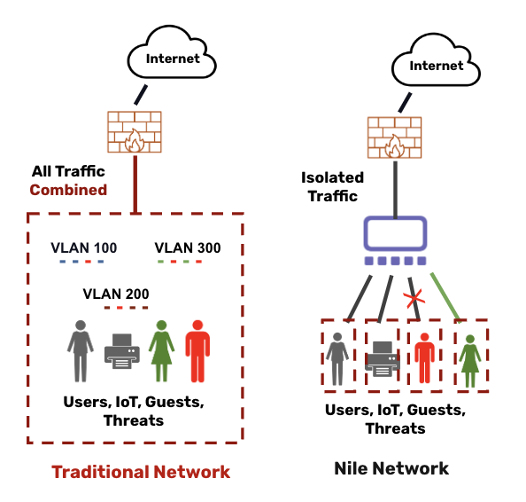
Given the risks, relying on users to do the right thing is not an option. Additionally, the use of VPN clients and trying to implement Opportunistic Wireless Encryption (OWE) and WPA3 to secure guest access connections are merely a stop gap with their own inherent security and usability flaws.
With Nile’s unique device isolation-centric architecture, you can quickly see how each internal and guest user, as well as IoT devices are completely isolated, delivering a foundational layer of protection at the network level. The isolation of individual users and devices eliminates VLANs and lateral movement and is the first step in building a network designed to combat modern threats.
While offering guest access provides convenient Internet access, IT organizations can now take advantage of modern zero trust network principles to protect their guests’ devices and data.
Conclusion
Nile offers an alternative that balances ease of use with zero trust security that’s crucial for today’s interconnected digital world. Not only are your guests’ devices more secure, so are your internal resources.
For organizations that are considering moving to an Internet Cafe Style model for guest Wi-Fi, the next blog on guest access will explain how to take advantage of our per-host isolation and up-level how you’re delivering and managing guest services throughout your organization in an efficient manner. And it’s scalable and secure!