
Nile-VeloCloud Integration Guide
This document describes the steps to integrate VeloCloud SD-WAN Edge appliances, in High Availability (HA) configuration, with the Nile Service Block (NSB). The desired result is a seamless integration between the Nile Access Service and the customer’s extended network, and thus with the Internet.
Overview
This document describes the steps to integrate VeloCloud SD-WAN Edge appliances, in High Availability (HA) configuration, with the Nile Service Block (NSB). The desired result is a seamless integration between the Nile Access Service and the customer’s extended network, and thus with the Internet.
The VeloClound appliances require manual configuration; no configuration of Nile NSB is necessary.
Prerequisites
- Four unique /30 Subnets – To implement a High-Definition and an Always-On service, the setup uses Equal Cost Multi-Path (ECMP) routing to configure four point-to-point links, to provide Layer 3 transit between the NSB and the VeloCloud Edge appliances.
- Administrative access to the VeloCloud Edge appliances.
Limitations
- The VeloCloud edge appliance cannot do static route with ECMP routing, so this guide uses OSPF for the L3 routing between the Nile gateways and the VeloCloud Edge appliances.
Topology
Both Nile gateways are active-active devices. It takes four unique ports to connect to the upstream edges (two each). VeloCloud is in Active/Standby mode; it requires 2 unique ports on the active and 2 unique ports on the standby appliance.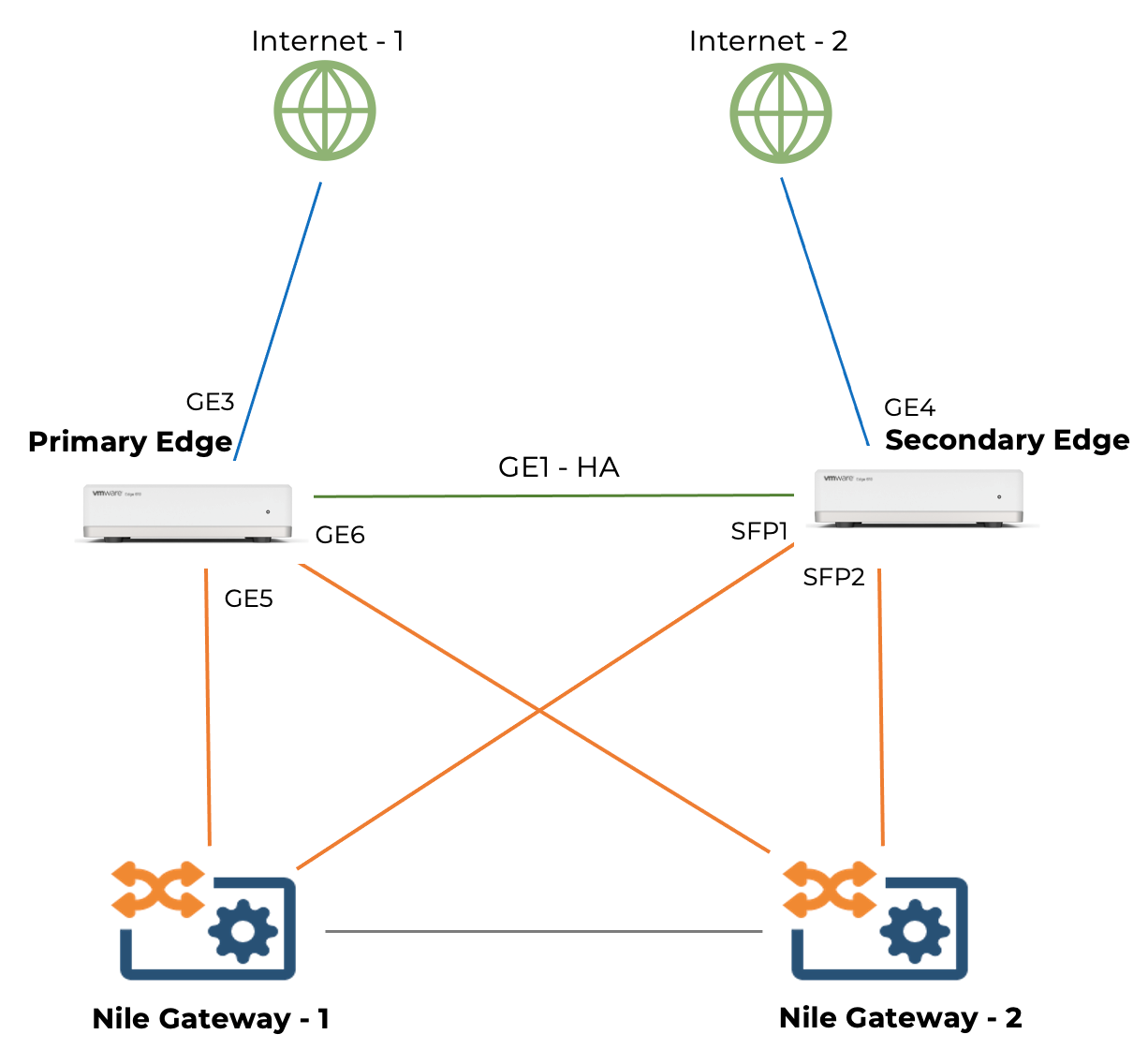
VeloCloud Interface Assignment
| GE1 | VeloCloud HA Link |
| GE3, GE4 | WAN Interfaces |
| GE5, GE6, SFP1, SFP2 | LAN Interfaces |
Configuration
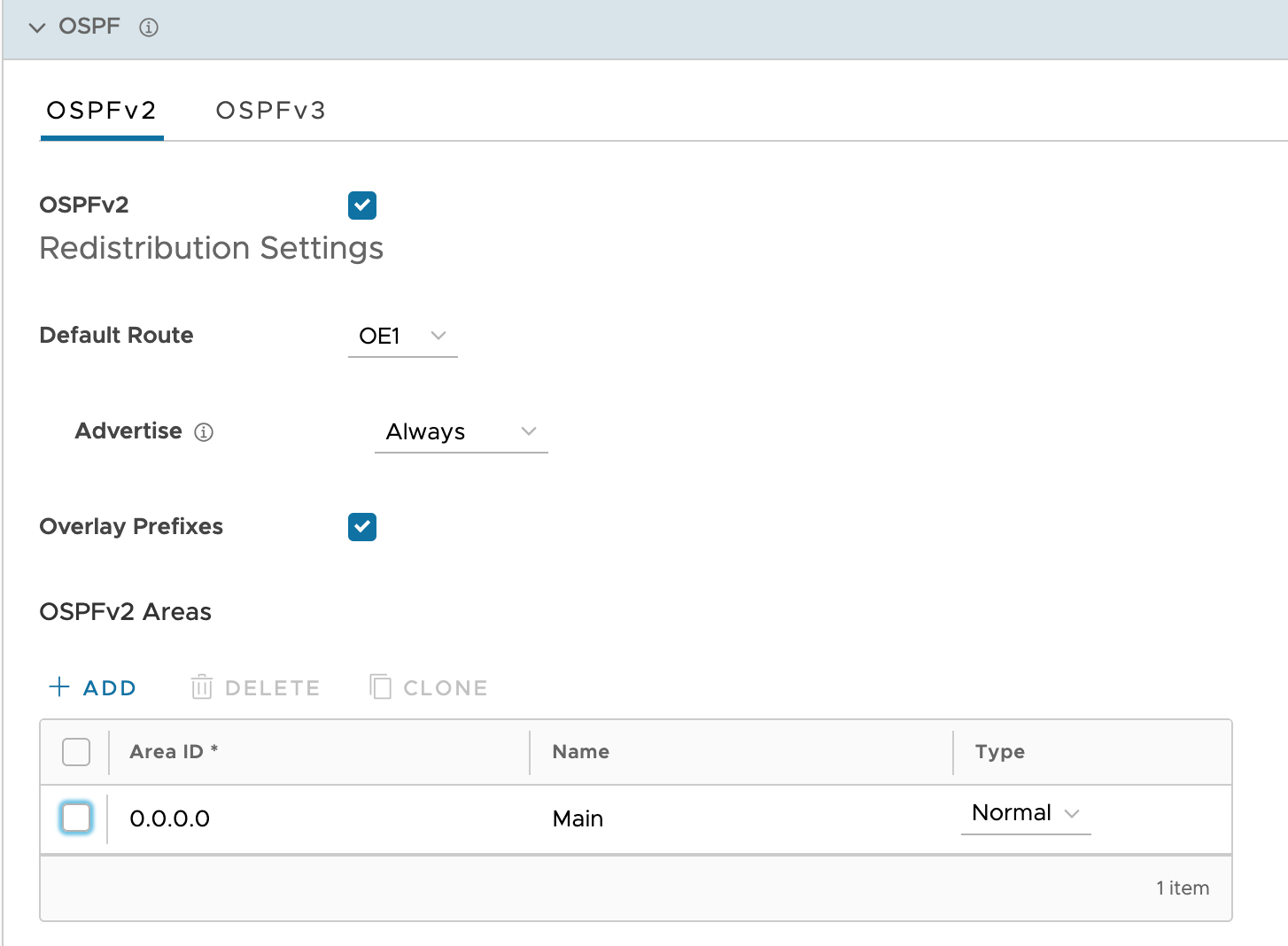
Enable OSPF
- Log into you VeloCloud Orchestrator
- Navigate to Profiles
- Click on the Branch Profile which is assigned to the Branch Edge that we are going to configure in this setup.
- Navigate to OSPFv2 and enable it, as shown below.
Configure the WAN side Interface
- Log into you VeloCloud Orchestrator
- Navigate to Edges
- Select your site-specific Edge Device
- Click on Configure
- Navigate to Interfaces
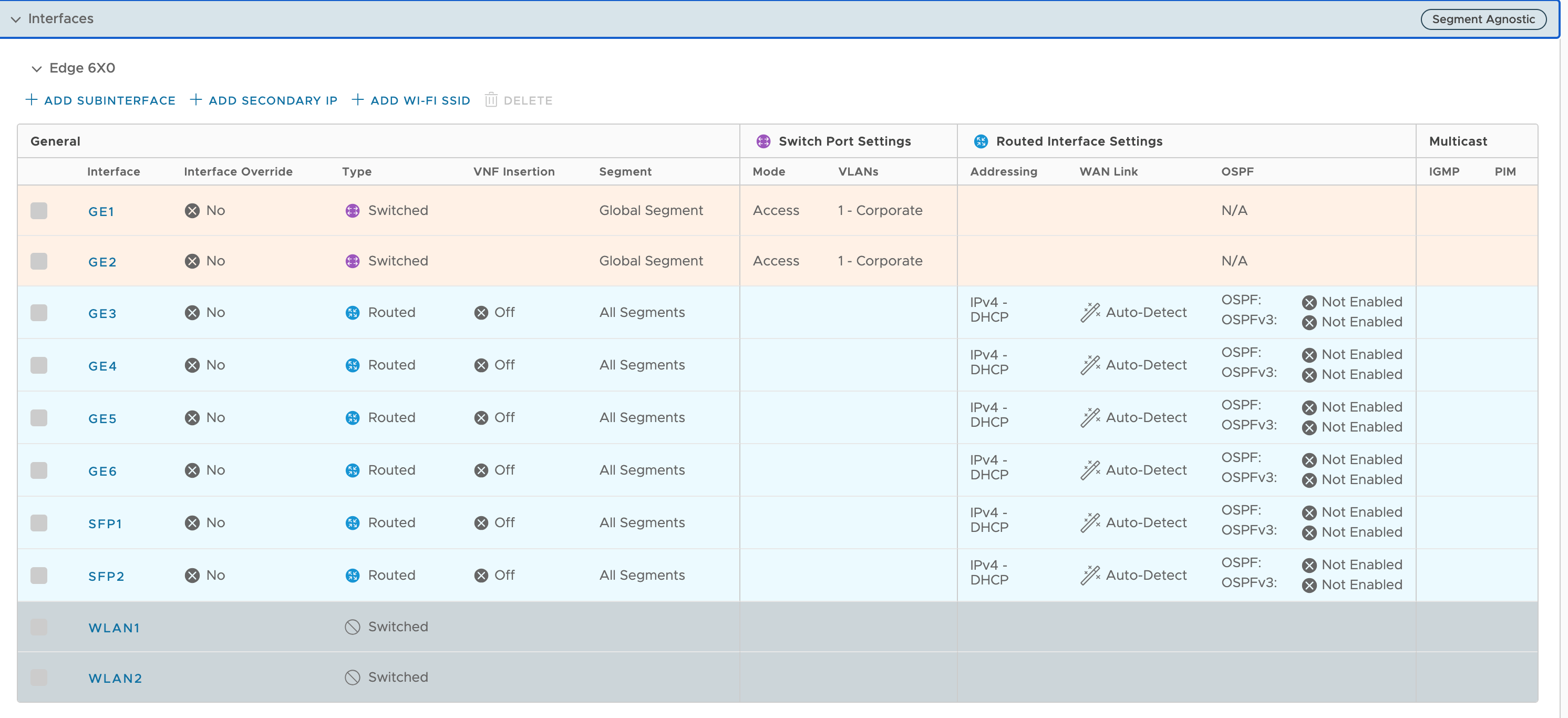
- Click on GE3
This example uses GE3 as the WAN Interfaces. It’s assumed you have two WAN providers
- In the IPv4 Settings Addressing Type drop-down list, choose one of DHCP, Static, or PPPoE. If “static” is chosen, use either (1) a private IP address with a NAT device in front of the edge, or (2) a public IP address. This example shows a public point-to-point IP link.
- Scrolling down, set the NAT Direct Traffic checkbox if a public IP address is specified in the Addressing Type data. Otherwise (1) uncheck this checkbox for a private IP address, and (2) provide a firewall or router that can NAT traffic outbound to the Internet.
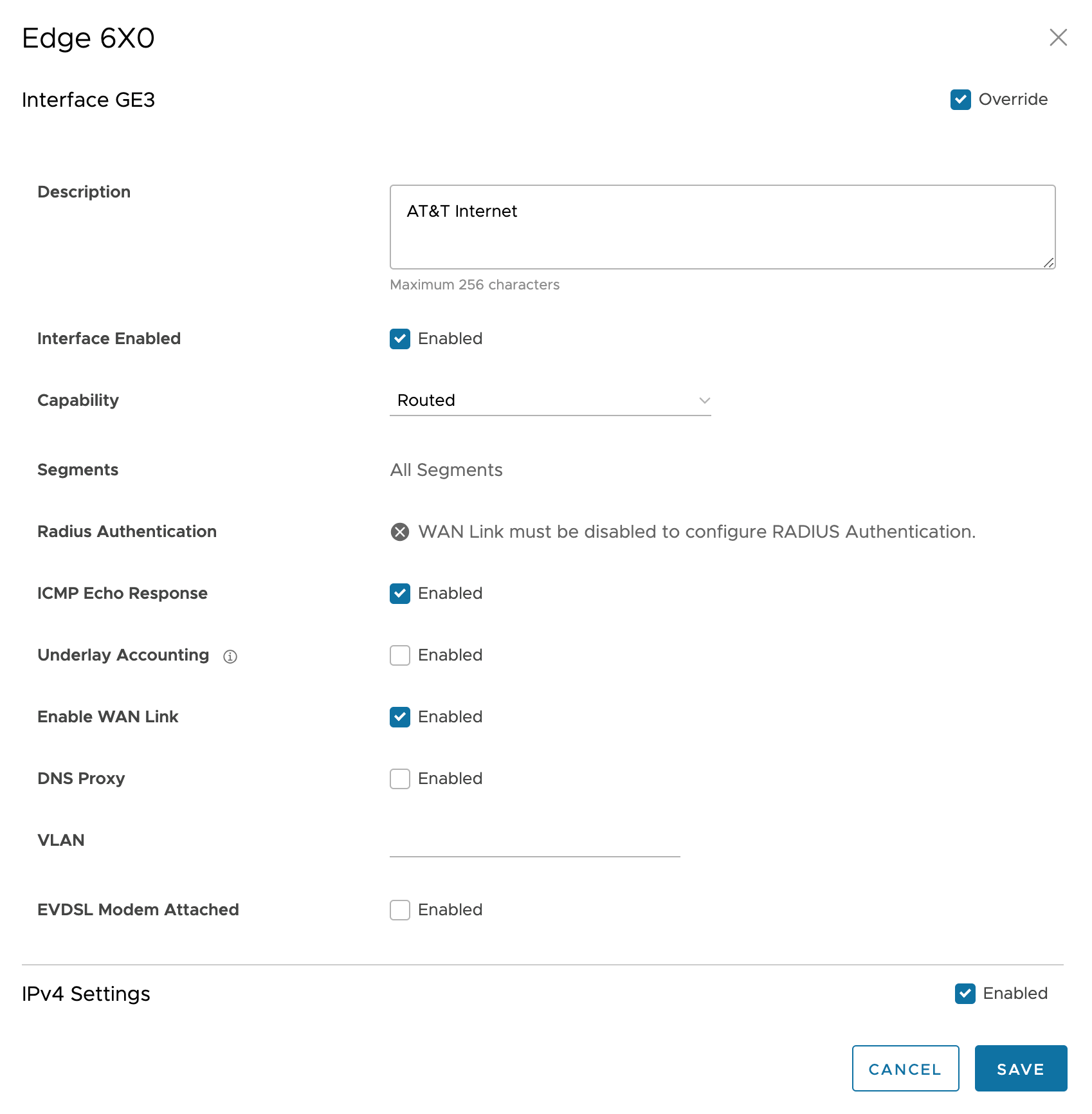
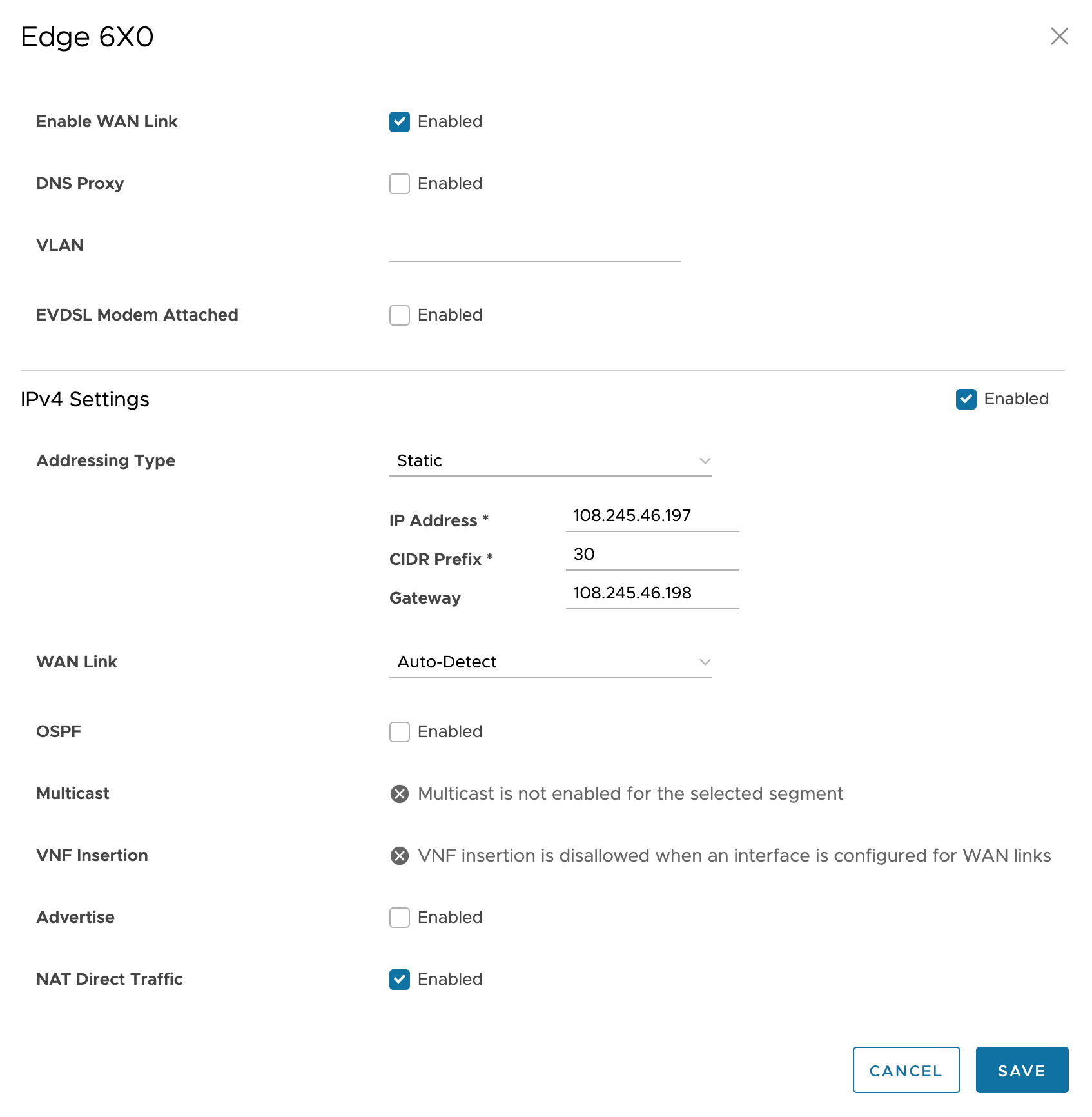
- Click the SAVE button
If you have a second WAN (Internet) interface, repeat the same steps for that interface as well. Use GE4 for the second WAN Interface.
Configure the LAN side interface
- Navigate to Interfaces and click on the GE1. In this example, GE1 and GE2 are the LAN side Interfaces connecting to the Nile Gateways
- Capability: if the Interface is in switched mode, change it to a routed port via the drop-down list.
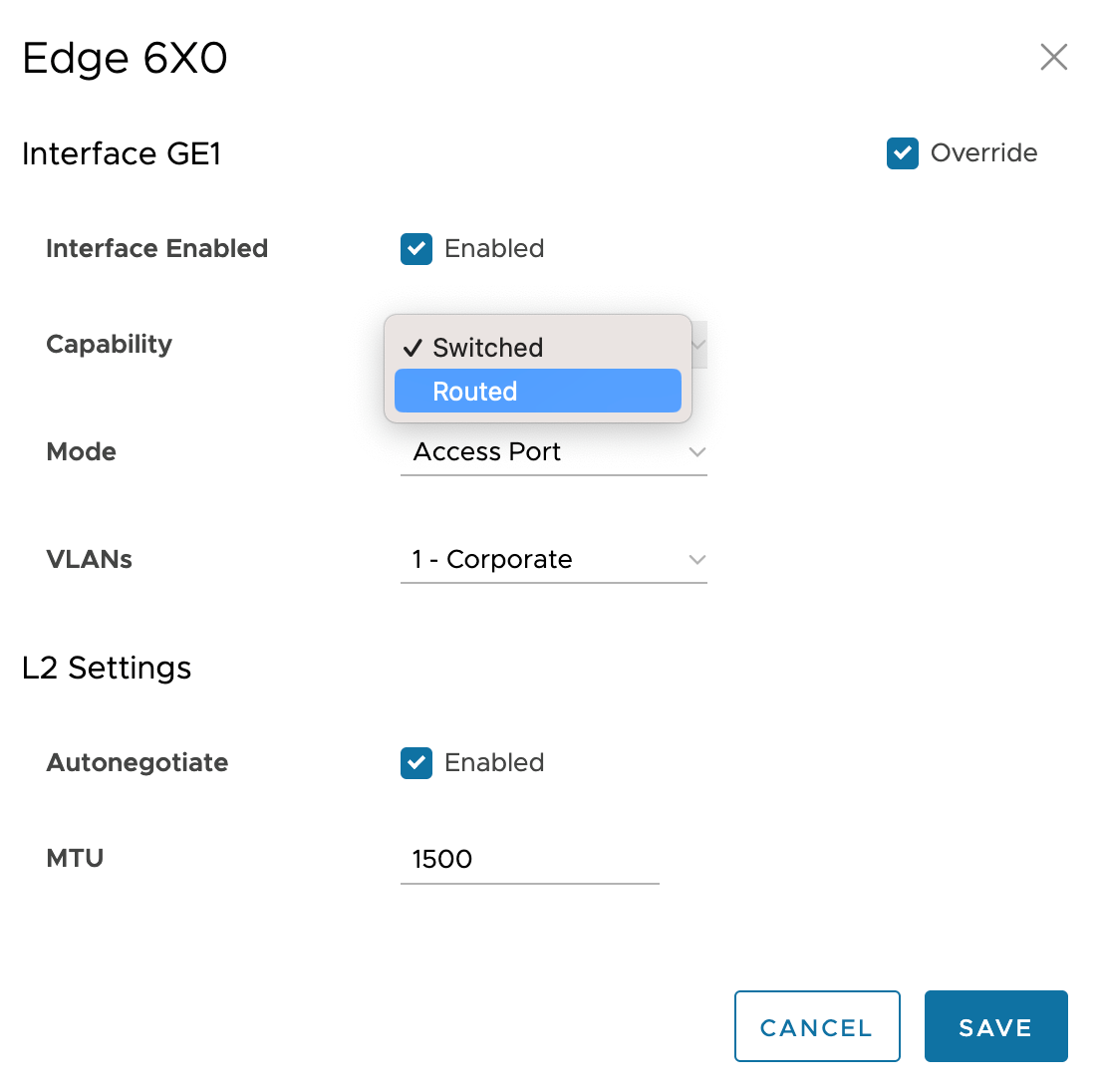
- Once you have selected the routed port, uncheck the checkboxes Underlay Accounting and Enable WAN Link
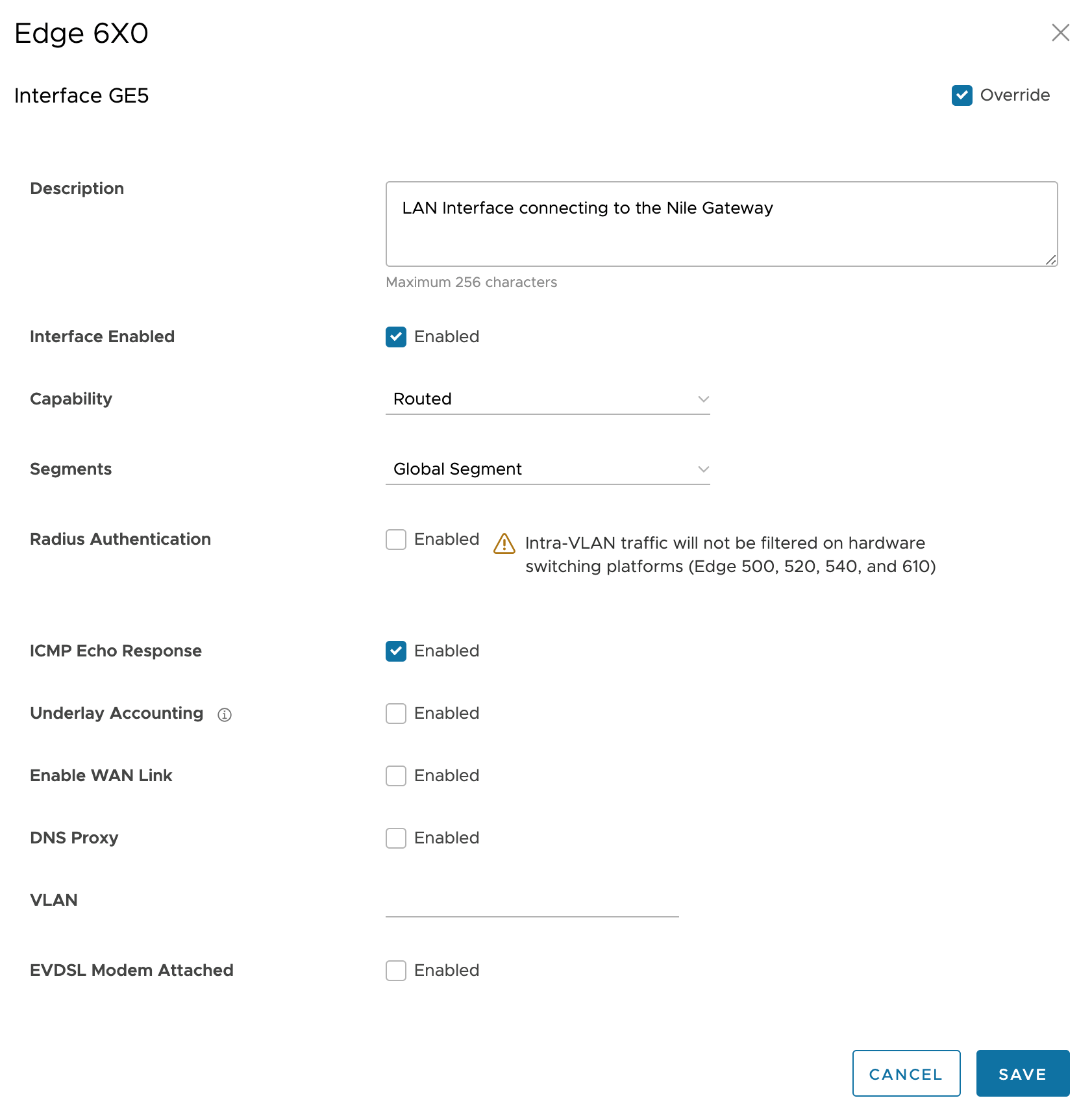
- IP Address: provide the IPv4 IP address to the interface. It is typically a /30 subnet.
- Click on the OSPF checkbox so that it’s checked.
- Click the Trusted Source checkbox so it’s checked.
- In the Reverse Path Forwarding drop-down, select “Not Enabled”. These two settings enable asymmetric routing among all the LAN-side interfaces.
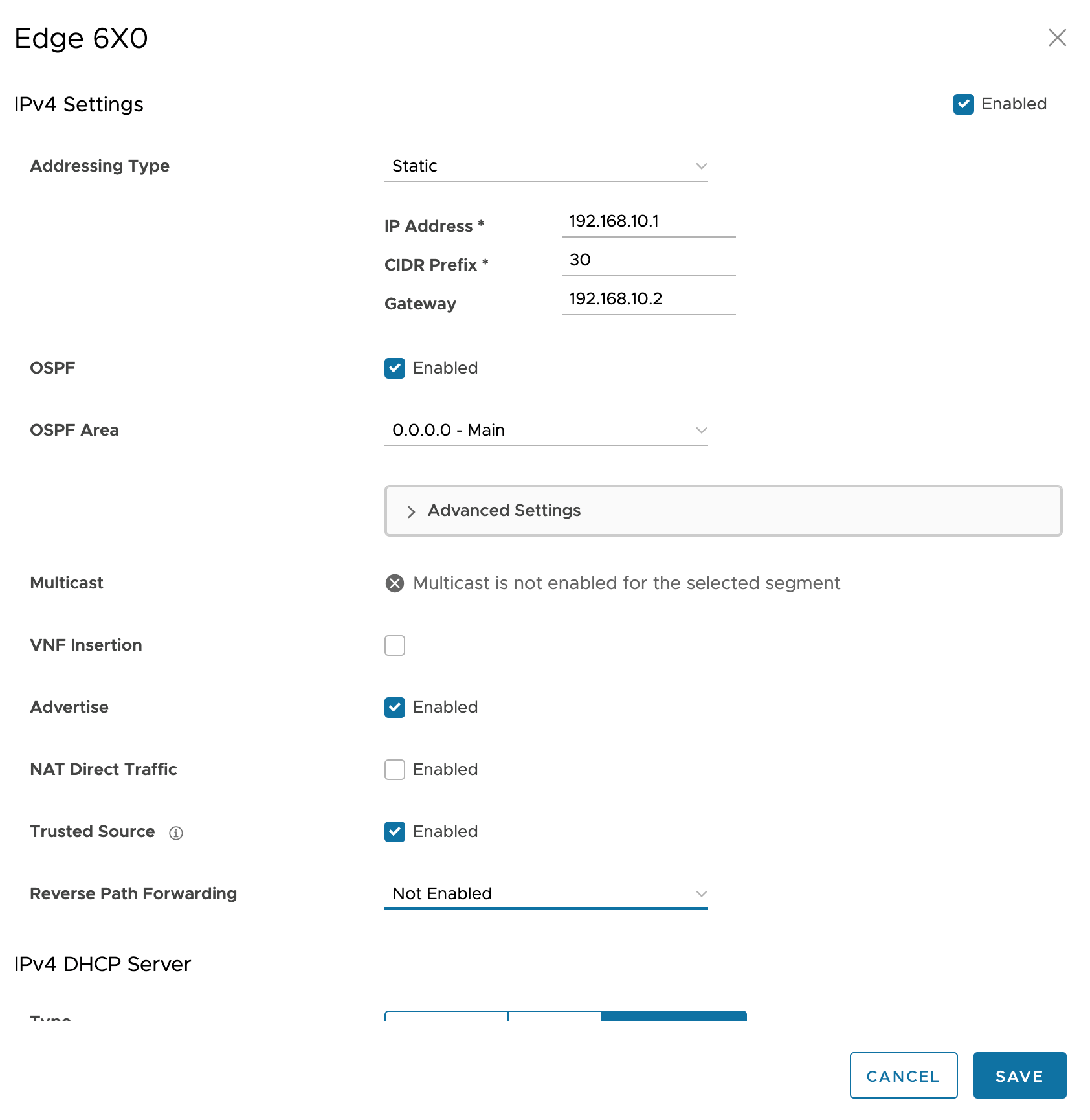
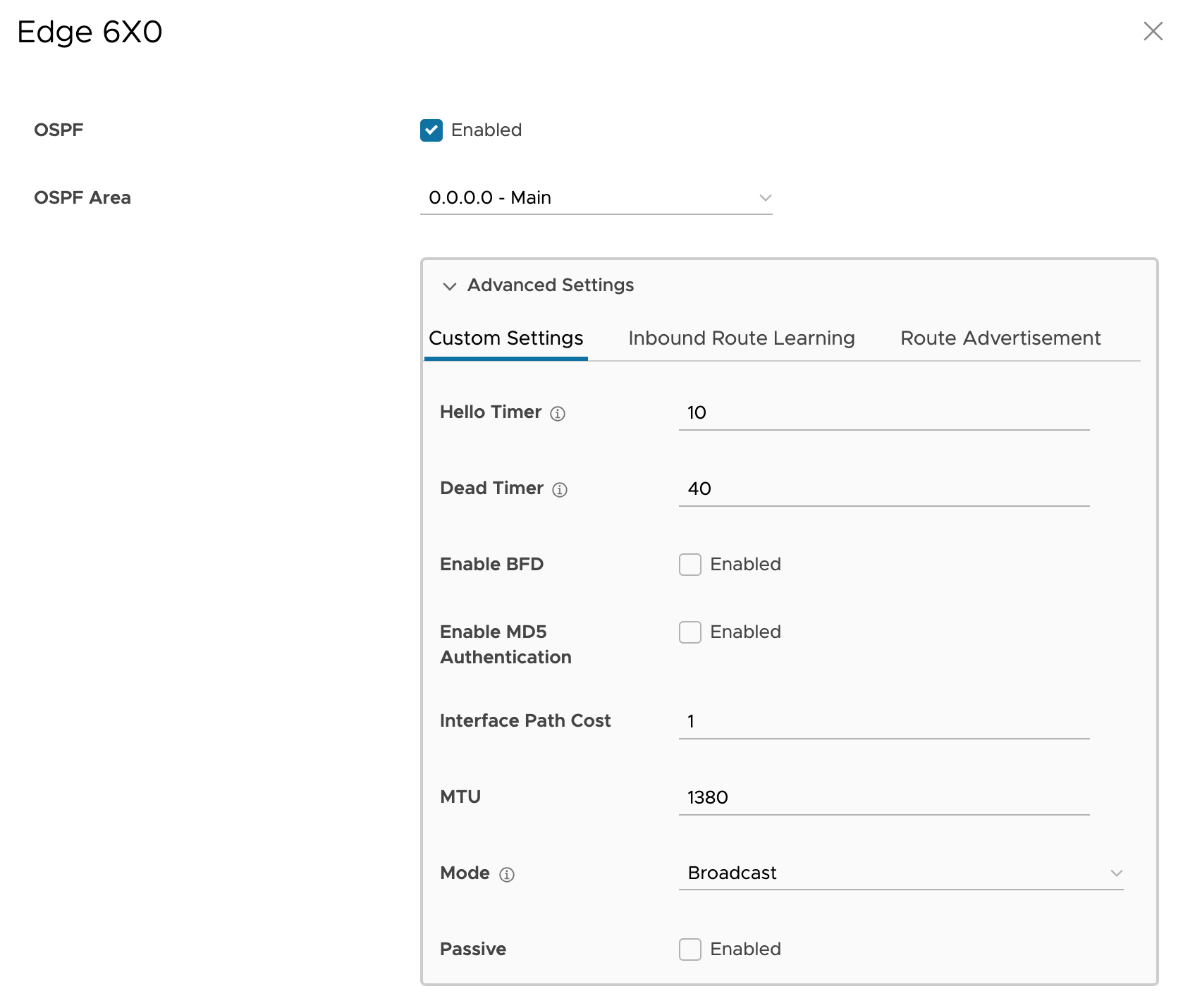
Configure OSPF settings
- On the same LAN interface configuration (GE3), click on Advanced Settings under OSPF.
- Keep the default settings as they are.
Inbound Route Learning
- Click on Inbound Route Learning tab
- Configure the settings as shown below
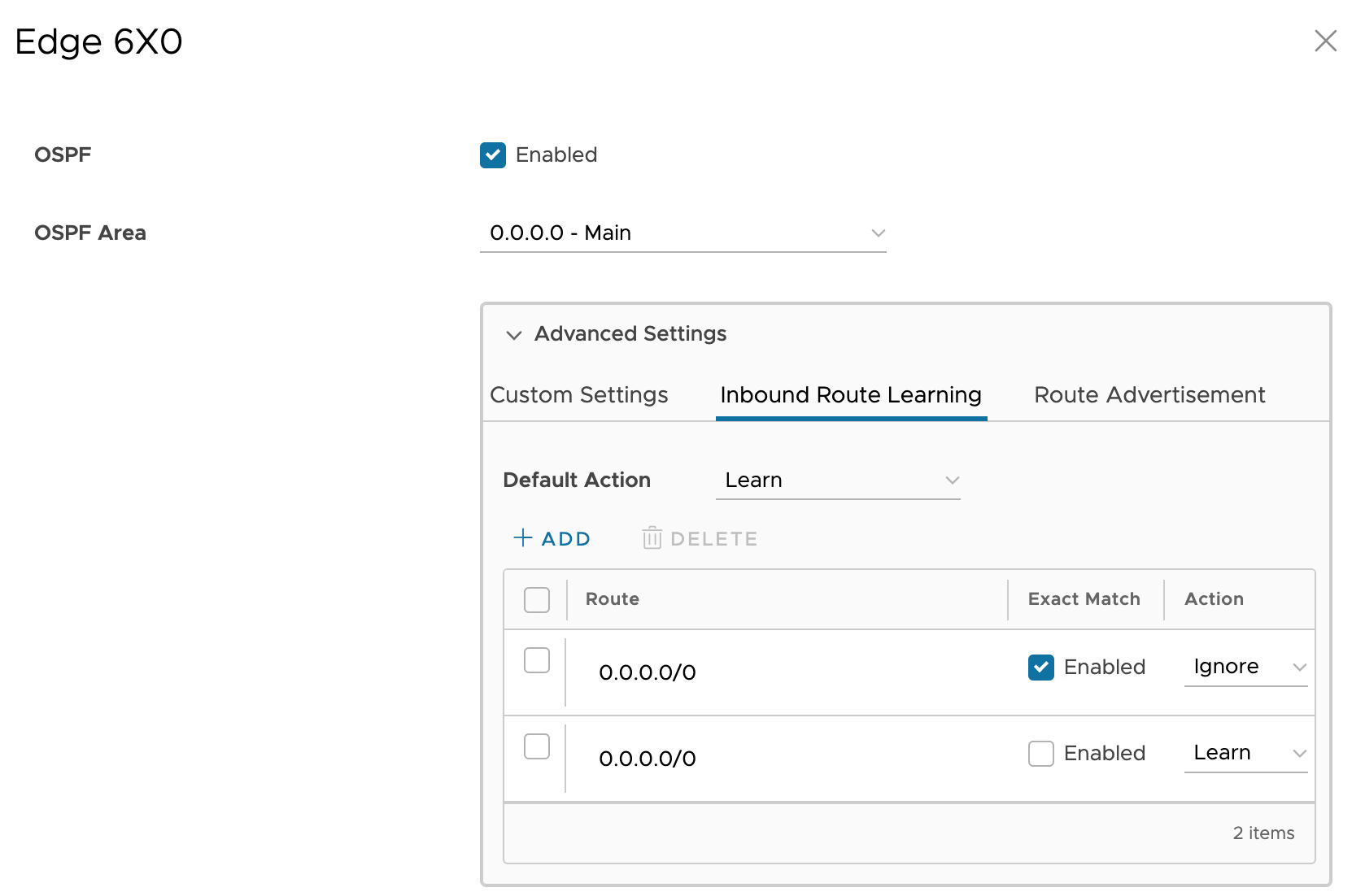
This configuration blocks the appliances from learning a default route inbound, and allows everything else. The VeloCloud Edge appliances learns all the NSB and user subnets as they are advertised by the Nile Gateways.
Route Advertisement
- Click on Inbound Route Learning
- Configure the settings as shown below
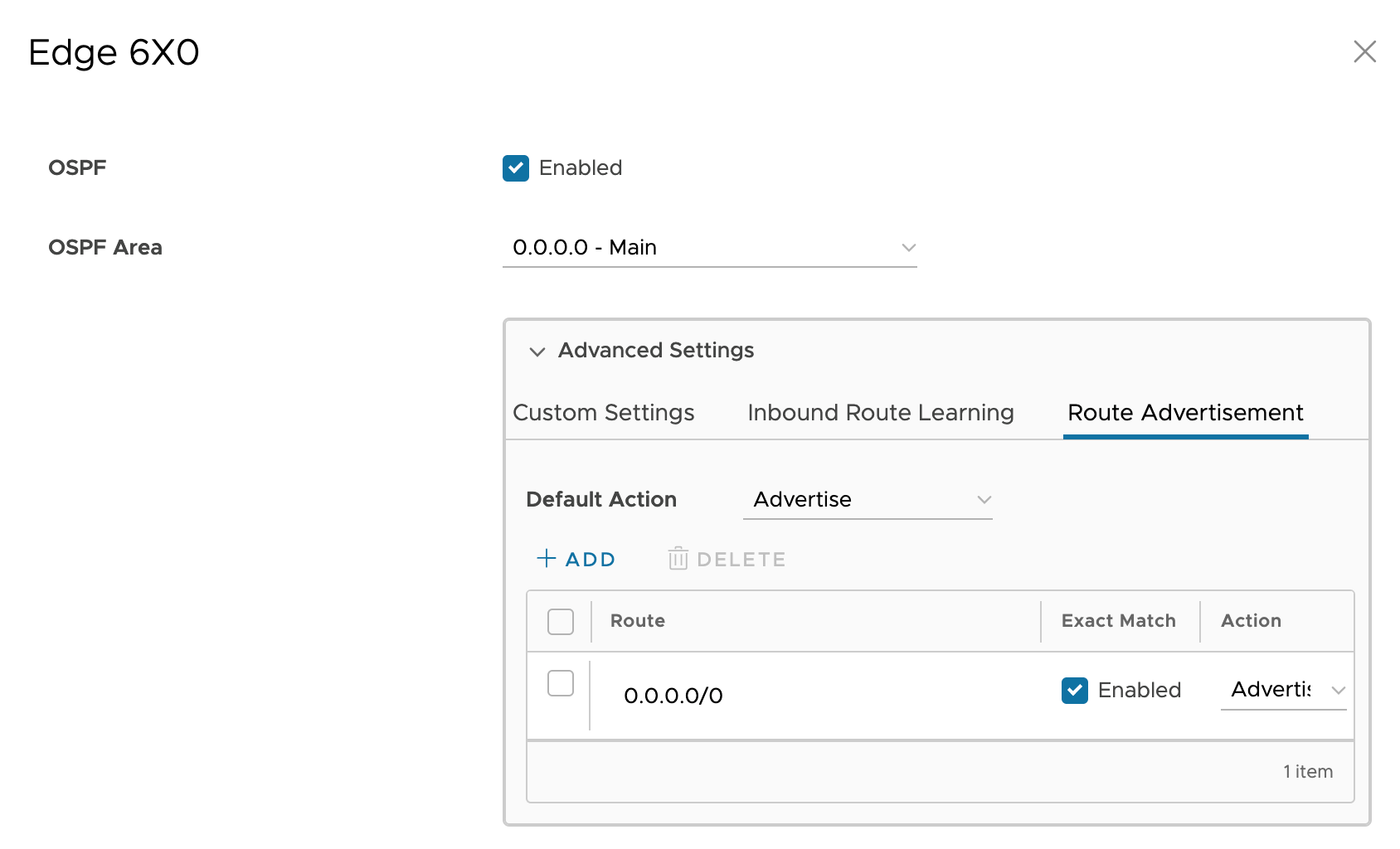
The VeloCloud Edge appliances advertise a default route to the Nile GW. This setting attracts all traffic towards itself.
- Repeat the above same steps for GE6, SFP1, and SFP2 LAN side interfaces. Make sure the /30 subnets are unique for each of these LAN side interfaces.