
Nile Solution Architecture: An Innovative Approach to Campus NaaS
Nile’s Modern Campus NaaS—the Nile Access Service—reinvents network design, deployment, and management, eliminating complexity and delivering a future-ready experience.
Introduction
Enterprise networks are falling behind. Outdated architectures—bogged down by manual configuration, rigid hardware, and reactive security—can’t keep up with the demands of cloud adoption, hybrid work, and AI-driven automation. The result? Bottlenecks, vulnerabilities, and inefficiencies that cripple modern businesses. Organizations now need intelligent, resilient, and automated networks to drive digital initiatives while controlling costs.
Nile’s Modern Campus NaaS—the Nile Access Service—reinvents network design, deployment, and management, eliminating complexity and delivering a future-ready experience. It streamlines operations through a cloud-native architecture, automation, and built-in security. By integrating cloud-native principles, AI Automation, and Campus Zero Trust security, Nile eliminates legacy infrastructure inefficiencies and bolt-on solutions to deliver a predictable, scalable, and cost-effective networking experience.
This paper explores the challenges surrounding traditional network architectures, highlights key features to consider when addressing these challenges, and ultimately showcases how Nile’s Campus NaaS model redefines networking forever using a secure approach to network design, deployment, and management. It outlines how Nile removes complexities, giving IT leaders a simplified, high-performance solution built for the future.
Traditional Network Architecture Challenges
Legacy enterprise network solutions suffer from layered complexity, inefficiencies, and high operational costs due to their rigid architectures, the inability to innovate across large portfolios, and the risk of disrupting established revenue streams. Because of this, organizations relying on traditional architectures encounter several key challenges:
1. Operational Complexity
Managing enterprise networks demands constant monitoring, troubleshooting, and manual intervention. IT teams are responsible for tuning countless variables and determining if default settings suit their unique environments. This often results in highly customized, ‘snowflake’ networks that are complex to manage and prone to inefficiencies, increasing both downtime risks and labor costs.
Additionally, most networks still depend on decades-old techniques and protocols—VLANs, access control lists (ACLs), manual QoS provisioning, Wi-Fi roaming configurations, and bolted-on NAC solutions. These legacy methods attempt to manage access dynamically but instead add complexity, increase the risk of outages, and create security vulnerabilities.
2. Limited Visibility and Reactive Management
Most traditional networks lack real-time insights with automated responses, forcing IT teams to troubleshoot and resolve problems after they impact users. Without proactive automation, IT staff must spend countless hours manually correlating logs and PCAPs, identifying root causes, and resolving connectivity issues that lead to the need for expensive add-on assistance tools like SIEM, etc. This leads to a higher Mean Time to Resolution (MTTR) and a devastating loss of IT and business productivity.
3. Security Gaps and Outdated Protection Mechanisms
Perimeter-based defenses assume that all internal traffic is trustworthy, leaving networks vulnerable to modern cyber threats. Legacy VLAN segmentation and ACLs are no longer sufficient to protect against today’s sophisticated cyberattacks. Attackers can easily exploit an individual device and move within a network laterally, bypassing firewalls and compromising critical systems within a Layer 2 VLAN.
IoT devices, known for weak security protocols, are increasingly targeted as entry points for malware. This allows malware to propagate quickly across the network and compromise sensitive data, underscoring the need for more robust, dynamic security measures to counter the evolving threat landscape.
4. High Costs and Inefficient Resource Allocation
Organizations are currently investing heavily in hardware, licensing, and IT personnel to maintain legacy networks due to outdated practices, complexity, and the constant need to manually fix issues, update software, and optimize performance variables. This often leads to inefficiencies in both time and resources. Additional costs arise from:
- Hardware Refresh Cycles: Legacy networks require costly refresh cycles every 5-7 years, forcing organizations to allocate substantial budgets and technical resources to replace aging infrastructure. These cycles are often unpredictable, requiring additional capital expenditure without necessarily improving network performance. As a result, businesses are continuously burdened with high upfront hardware, software, licensing, and labor costs that require diverting resources that could be better allocated elsewhere.
- Inefficient Scaling and Capacity Planning: Traditional network models often require organizations to overprovision infrastructure in anticipation of future needs, leading to underutilized resources and wasted costs. Alternatively, underprovisioning risks performance gaps and the need for costly upgrades down the line. Without the ability to scale dynamically, organizations face significant inefficiencies in resource allocation, especially as demand fluctuates.
- Expensive Troubleshooting and Professional Services: Managing, securing, and optimizing legacy networks requires specialized expertise, which can be challenging to find. As a result, organizations often face higher-than-anticipated costs for professional services. These services typically involve extensive diagnostics and tailored solutions and bolted-on AI, consuming internal resources and escalating operational expenses. The complexity of maintaining a network built on fully or partially out-of-date systems also raises the risk of service disruptions, which can harm productivity and impact customer satisfaction.
Addressing Challenges in Traditional Campus Networks
As industry dynamics and business requirements continue to evolve, it’s crucial to explore alternatives that offer greater alignment and help organizations navigate an increasingly complex technological landscape:
1. AI Automation for Smarter Network Operations
As enterprise networks expand and become more complex, AI Automation is key to managing operations efficiently. It enables real-time optimization and fault remediation, automatically adjusting traffic flows and bandwidth based on usage patterns to maintain peak performance. QoS and Wi-Fi roaming settings are also auto-provisioned. Finally, AI built to support a modern architecture provides predictive maintenance by identifying potential issues early, enabling the system to self-correct and prevent disruptions before they impact operations.
Beyond lessening manual configurations and increasing performance and reliability, AI strengthens security by automating threat detection and response. It can proactively identify vulnerabilities and stop potential threats before they’re exploited. By handling routine tasks and accelerating decision-making, AI Automation allows IT teams to focus on strategic initiatives, driving greater efficiency and innovation.
2. Built-in Campus Zero Trust
The shift from perimeter and layered security models to a native Zero Trust framework is transforming the way enterprise networks are protected. Zero Trust eliminates the assumption that internal network traffic can be trusted, requiring verification at every point. This model has traditionally involved complex authentication and segmentation techniques using add-on solutions to ensure that users and devices only have access to the resources they need. New innovations significantly streamline this process, where native Campus Zero Trust capabilities are built directly into the network architecture.
- Zero Trust Access simplifies network security with built-in solutions for onboarding users and devices of all types, including employees, students, contractors, guests, and IoT devices, eliminating the need for external NAC solutions, appliances, and complex segmentation, allowing for the enhanced security of internal data and resources.
- Secure Authentication ensures every device and user is verified before accessing the network, removing the complexity of managing separate authentication tools, moving away from complex NAC solutions, and providing users with a consistent workflow whether connecting to wired or wireless networks, on-premises, or remote.
- Continuous Authorization provides ongoing re-verification of device and user behavior, ensuring immediate detection of changes and reducing the risk of undetected threats.
- Streamlined Device Isolation architecture that places each device into a segment of one delivers enhanced security that extends to guest and IoT onboarding, minimizing helpdesk involvement and enabling users to independently onboard IoT devices, easing the IT resource burden.
- Campus Zero Trust Policy enhances network control by integrating threat containment with existing firewalls or SSE solutions. It combines visibility, lateral movement prevention, and intelligent policy enforcement.
- Zero Trust Policy Enforcement supports granular monitoring, quickly detecting and responding to malware using comprehensive firewall and SSE capabilities, enabling faster threat mitigation.
- Device Behavior Visibility continuously detects abnormal behavior, mitigating risks like MAC spoofing and ensuring early threat containment.
3. Scalable and Predictable Networking with Campus NaaS
Campus Network-as-a-Service (NaaS) adoption is gaining momentum as organizations seek to reduce capital expenditures associated with traditional network infrastructure. By shifting to subscription-based models, enterprises avoid the high upfront costs of purchasing and maintaining hardware while benefiting from flexible, scalable, and on-demand network solutions.
Campus NaaS, combined with a standardized architecture model, allows companies to better align their wired and wireless LAN expenditures with actual usage, improving budget predictability and operational agility. Additionally, Campus NaaS providers are offering natively integrated AI, security, and management tools, which allow enterprises to gain access to advanced features without having to invest in additional resources or infrastructure.
4. Reduced Costs and Optimized Resource Allocation
Legacy networks are often burdened by high operational costs, rigid scaling, and inefficient resource use. Frequent hardware refreshes, overprovisioning, and costly manual maintenance lead to unpredictable expenses and IT operations strain. Modern network architectures, built on cloud—and security-first principles with AI-driven automation, address these issues through intelligent optimization and flexible consumption models, enhancing efficiency while reducing costs.
- Eliminating Costly Hardware Refreshes: Modern architectures shift from CapEx-heavy models to predictable OpEx alternatives by leveraging subscription-based or Network-as-a-Service (NaaS) approaches. Cloud-native designs decouple hardware and software lifecycles, enabling continuous updates without expensive refreshes, while vendor-managed upgrades ensure devices remain optimized and secure.
- Intelligent Scaling and Capacity Optimization: Rather than relying on reactive scaling methods, Nile continuously monitors network capacity and throughput, dynamically identifying when additional hardware is needed to meet increased capacity and throughput demand. This proactive approach ensures optimal performance without excess infrastructure, while the pay-as-you-grow model aligns costs with actual usage, enhancing budget predictability.
- Reducing Operational Overhead: With AI Automation and self-optimizing capabilities, modern networks minimize manual intervention, lowering troubleshooting costs. Interactive and intuitive orchestration platforms further streamline operations, reducing the need for specialized IT resources and expensive professional services.
Nile’s Revolutionary Architecture: Forever Eliminating Network Challenges
The Nile Access Service addresses all pain points of traditional campus wired and wireless network architectures by offering an AI-powered, cloud-first Campus NaaS solution that removes operational burdens and ensures always-on performance with a financially backed 99.95% Performance Guarantee.
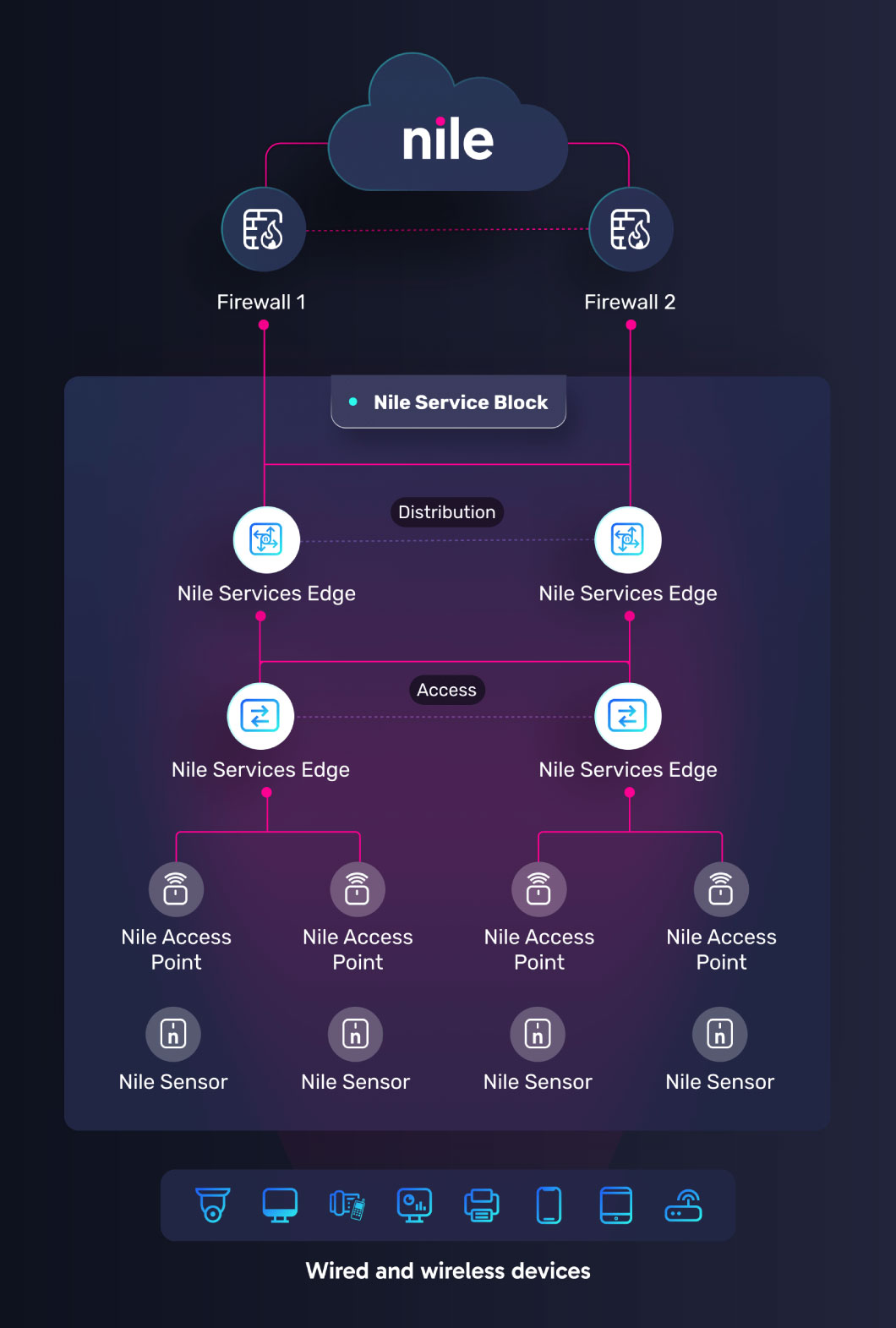
We combine high-performance wired and wireless infrastructure with microservices-based software, delivering seamless integration of Zero Trust, extensible APIs, and cloud management orchestration. AI Automation handles complex and repetitive tasks, freeing up IT resources while providing customers with full visibility and control over their network operations.
Here’s how the architecture comes together.
A Radically Simplified Network Model
Nile’s network deployment model uses a standardized and deterministic design called a Nile Service Block (NSB) for every location, regardless of business type or size. This consistent and predictable approach streamlines critical processes such as network site surveys, architecture planning, licensing, BoM creation, and underlay configuration with AI precision. This ensures highly accurate deployments, faster rollouts, and optimized performance that leads to happier users, fewer help desk tickets, and less time spent troubleshooting or engaging with slow-to-respond vendor support teams.
Engineered for Limitless Scale and Agility
The NSB’s modular design enables effortless scalability, allowing organizations to expand network capacity or add new locations simply by deploying additional service blocks. Whether scaling across campuses or within multi-story facilities, the system maintains predictable performance at any scale. AI Automation ensures real-time resource allocation, bandwidth optimization, and policy adjustments, providing operational agility without manual oversight.
Security-First Hardware and Software Engineered for Maximum Protection
Security is a foundational element of the Nile Service Block. Every component is designed to minimize vulnerabilities and safeguard network integrity from day one. The infrastructure is secure by default, featuring:
- Hardened configurations to reduce exploitable points of entry.
- No console access, eliminating common internal attack vectors.
- Trusted Platform Module (TPM) for hardware-based protection.
- MACsec encryption to secure data in transit.
This security-first hardware and software approach guarantees that your network stays protected as it grows—without the complications of add-on solutions.
Enterprise-Grade Resiliency and Always-On Availability
Network uptime is essential for sustaining productivity, enhancing user experience, and ensuring business continuity. Nile’s architecture focuses on resiliency and high availability, which enables campus networks to endure failures and unplanned outages, adapt to sudden demand increases, and sustain optimal performance—all without introducing complexity or operational burdens.
Built-In Redundancy for Continuous Operations
The foundation of Nile’s resiliency strategy lies in its NSB, which is architected with full redundancy to eliminate single points of failure and maintain seamless connectivity. Key features include:
- High-availability hardware with dual power supplies and multi-path connectivity to maintain uptime.
- Redundant uplinks and failover paths that reroute traffic instantly during link or hardware failures.
- Intelligent Traffic Management that identifies latency-sensitive traffic for optimal network transmission without the need to manage QoS policies.
This design guarantees that traffic flows stay uninterrupted, even during hardware malfunctions or network disruptions, allowing users to experience no service degradation.
The Industry’s Only Financially Backed 99.95% Performance Guarantee
Nile stands behind its architecture model with a 99.95% financially backed uptime guarantee, giving organizations confidence that their network will perform reliably. This Performance Guarantee provides:
- Predictable, high-performance networking with almost zero downtime.
- Financial accountability if uptime targets are not met.
- Reduced operational risk through built-in safeguards and proactive management.
Zero Trust Security Architecture: Built for Absolute Protection
In today’s evolving threat landscape, perimeter-based security models are no longer sufficient in enterprise campus networks. Attackers are increasingly exploiting internal vulnerabilities, using tactics like lateral movement and credential theft to bypass traditional defenses. Nile’s Zero Trust security architecture eliminates these gaps by embedding zero trust security directly into the network’s foundation—across both wired and wireless connections—ensuring that no user, device, or application is trusted by default.
1. Native Zero Trust Across Wired and Wireless Networks
Nile recognized the limitations of bolted-on security and intentionally designed the network to integrate Zero Trust directly into the core architecture. This built-in approach removes the need for complex overlays or third-party tools, simplifying security operations while enhancing protection.
- Consistent Security Across the Entire Network: Whether users connect through wired ports or Wi-Fi, every connection is scrutinized equally.
- Identity-Centric Access Control: Every user, device, and application must authenticate before gaining network access, regardless of location or role.
- Device Isolation by Default: The Nile network isolates traffic at a device level using a segment-of-one approach. This approach ensures that all traffic flows are inspected, prevents unauthorized lateral movement, and strictly limits the potential blast radius of security incidents.
2. Continuous Authentication and Real-Time Threat Prevention
Unlike a traditional model, which authenticates users only at the point of entry, Nile’s architecture enforces continuous authentication, ensuring security throughout every session.
- Ongoing Identity Verification: User and device behavior is continuously monitored. Any deviation from expected behavior triggers re-authentication or automatic disconnection.
- Dynamic Policy Enforcement: Access policies adapt in real time based on user roles, device health, and location, reducing the risk of compromised credentials leading to unauthorized access.
3. Compliance-Ready by Design
Regulatory compliance is a critical consideration for many organizations. Nile’s Zero Trust architecture helps meet stringent security requirements while simplifying audit processes. Nile has achieved several key certifications that validate its commitment to security, privacy, and operational integrity:
- SOC 2 Type II Certification: Demonstrates that Nile maintains rigorous controls to safeguard customer data, focusing on security, availability, processing integrity, confidentiality, and privacy.
- ISO 27001 Certification: ISO 27001 is the globally recognized standard for information security management. It certifies that Nile follows best practices for managing sensitive information, including systematic risk management and continuous security improvement processes.
- CSA STAR Level 1 (Cloud Security Alliance): Nile’s inclusion in the CSA STAR registry highlights its commitment to cloud security transparency, evaluating adherence to cloud security best practices, including data protection and risk mitigation strategies.
- Wi-Fi CERTIFIED™ Ensures that Nile’s wireless solutions meet industry-agreed standards for security, interoperability, and reliability, providing customers with secure, high-performance wireless connectivity.
4. Effortless Security Management—No Complexity, No Compromise
Traditional Zero Trust implementations often necessitate extensive configuration and continuous management. Nile simplifies this by embedding security features directly into the network, extending from our Infrastructure to Access and Policy Layers. This approach reduces the burden on IT teams by minimizing the need to add external solutions, undertake integration efforts, and maintain these services, all while enhancing overall protection.
- No Need for External NAC Solutions: User and device onboarding, authentication, and policy enforcement are all handled natively within the Nile platform.
- Unified Orchestration: Security policies and access controls can all be managed through the Nile Control Center, offering IT teams a single pane of glass for end-to-end visibility.
- Automated Threat Containment: When a threat is identified, the service employs tightly integrated firewall or SSE solutions to dynamically block malicious traffic or isolate affected devices in real time without manual intervention.
Integration and Extensibility Architecture
Enterprise networks must integrate effortlessly with a wide range of security, monitoring, and management tools to ensure cohesive operations and streamlined workflows. Nile’s modern network architecture is designed with integration and extensibility at its core, enabling IT teams to connect Nile’s Campus NaaS platform with existing ecosystems while maintaining agility and control. Whether it’s security platforms, cloud services, or IT management tools, Nile ensures seamless interoperability and future-ready scalability.
1. API-first Design for Custom Integrations
Nile’s architecture is built with an API-first approach, empowering IT teams to create tailored integrations that meet their specific operational needs. Using extensible RESTful APIs, organizations can easily connect Nile’s platform to existing systems and automate network management tasks.
- Custom Workflows: Built-in integrations with ITSM platforms like ServiceNow for automated ticketing, incident management, and change tracking.
- Real-Time Data Sharing: Export of real-time network data into analytics platforms for deeper insights into performance, usage trends, and security events.
- Automation and Orchestration: Integration with DevOps tools to streamline provisioning, configuration management, and automated responses to network events.
2. Security Ecosystem Integration
Maintaining a strong security posture requires collaboration between networking and security tools. Nile’s platform integrates seamlessly with leading security solutions, ensuring end-to-end protection and compliance.
- SSE Integration: Extend Nile’s Zero Trust enforcement to Secure Service Edge (SSE) solutions like Zscaler Internet Access, Palo Alto Prisma, and Microsoft Entra for holistic security coverage.
- SIEM Compatibility: Nile generates detailed logs and event data that can be fed into Security Information and Event Management (SIEM) platforms for advanced threat detection, correlation, and forensic analysis.
- Identity and Access Management (IAM): Integrate with directory services such as Active Directory (AD), Azure AD, or Okta for centralized user authentication and policy enforcement using modern Single Sign-On (SSO) or traditional 802.1X or MAC authentication methods.
3. Future-Ready Extensibility
Nile’s open architecture ensures that organizations can adapt to technological changes and integrate with new tools and platforms as they emerge.
- Support for Evolving Standards: Built to align with evolving LAN and security protocols and frameworks, ensuring long-term interoperability.
- Partner Ecosystem: Leverage a growing ecosystem of validated technology partners to extend network capabilities without additional complexity.
- Developer-Friendly Ecosystem: Nile’s well-documented APIs and SDKs enable developers and IT teams to build custom integrations and automation tailored to unique business needs.
Nile AI Automation Center: Enabling Intelligent Operations
The AI Automation Center, part of the Nile Services Cloud, leverages Nile’s Digital Twin technology combined with closed-loop automation to predict possible issues and seamlessly automate remediation. The Digital Twin is a virtual replica of each network that continuously maps, monitors, and simulates behavior using real-time and historical telemetry sent from the customer NSB.
When paired with AI Automation, this powerful combination enables the system to detect, diagnose, and resolve issues without manual intervention—streamlining operations and minimizing downtime. By harnessing real-time data analytics and AI modeling, Nile ensures optimized performance, proactive maintenance, and rapid problem resolution, setting it apart from traditional network solutions. A patented verification model even ensures that software upgrades perform as expected before allowing users to reconnect.
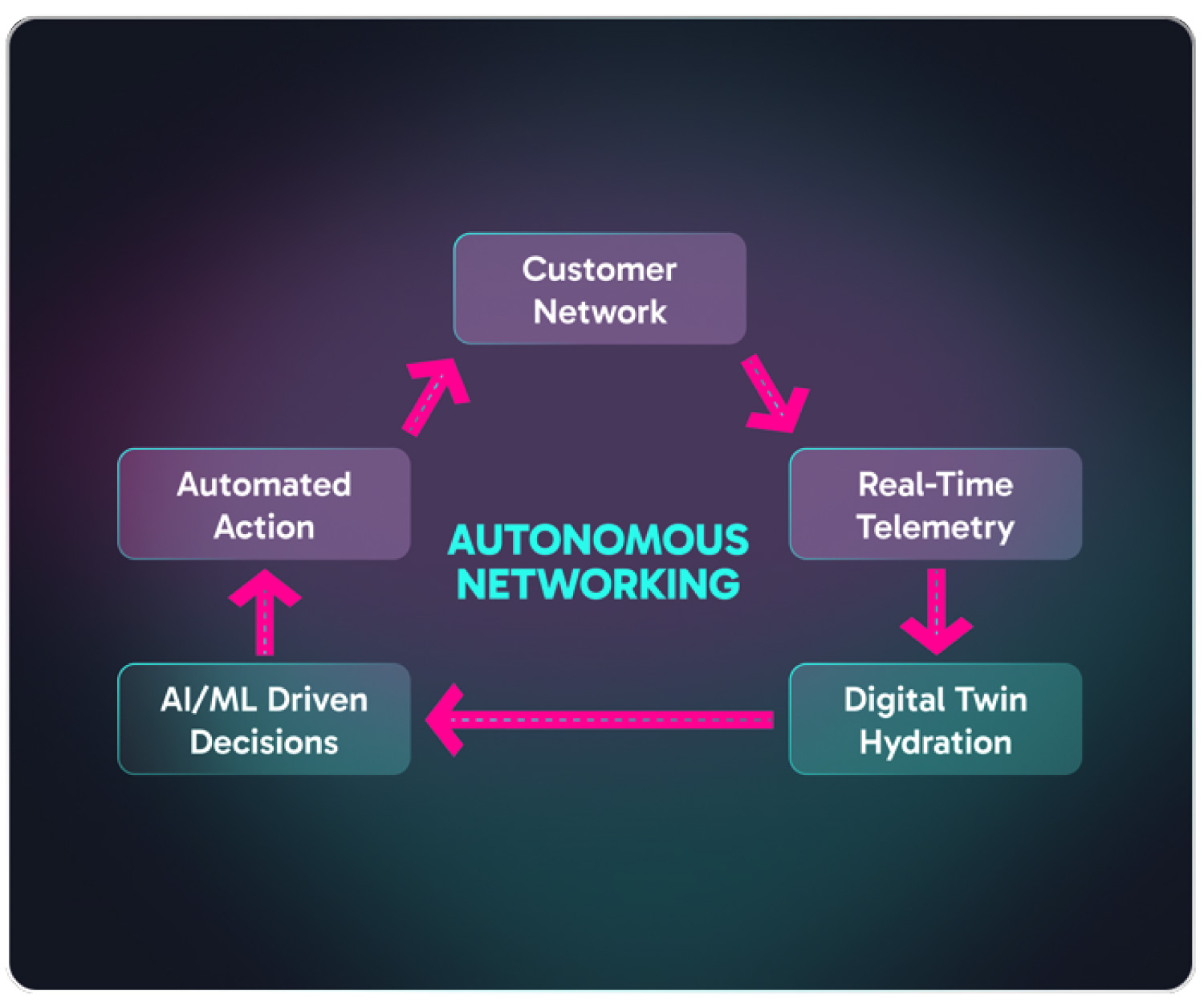
Capabilities include:
- Intelligent Network Assurance: Detects anomalies, predicts failures, and proactively resolves issues to prevent disruptions and reduce IT workload.
- Adaptive Performance Optimization: Continuously adjusts to changing demands in real time for peak efficiency.
- Automated Software Updates: Ensures Nile network devices are continuously patched and updated without human intervention, strengthening security and maintaining peak performance.
Nile’s AI and Deterministic Systems: Proven to Eliminate Network Issues
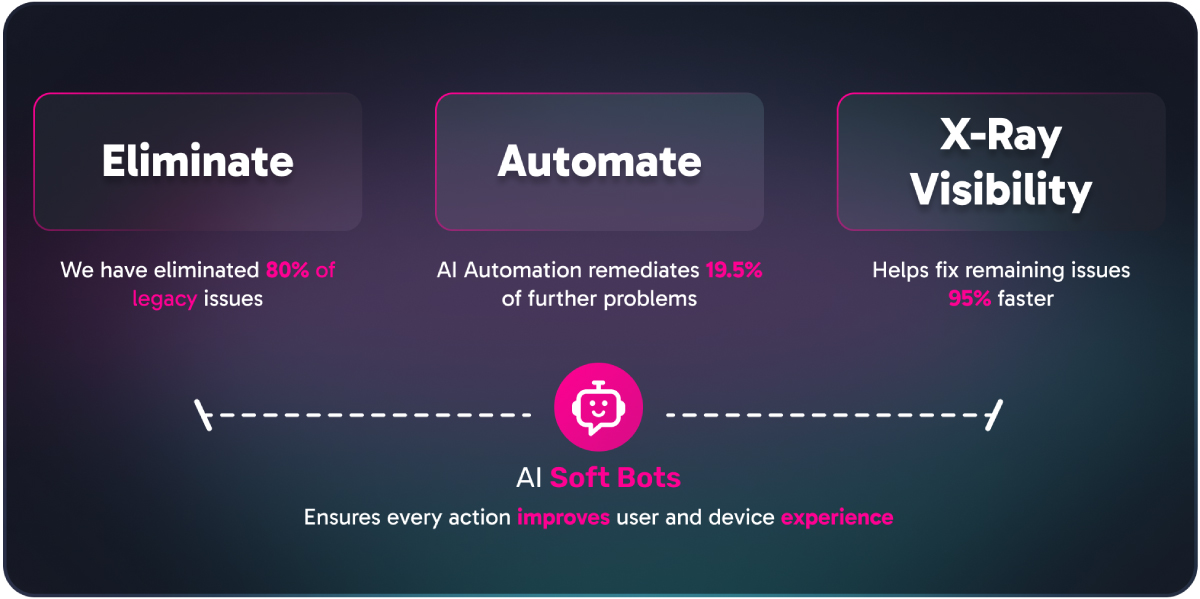
Nile’s closed-loop, standards-based deterministic design immediately eliminates 80% of the most common legacy network issues. AI automation then takes over, identifying and remediating another 19.5% in real time. For the final 0.5% of complex issues, deep telemetry and X-Ray Visibility empower our support team to resolve them swiftly. Meanwhile, AI Soft Bots continuously learn and refine operations, ensuring ongoing improvements to user and device network experiences.
Service Visibility and Control: Complete Oversight, Effortless Management
IT teams and end users benefit from two intuitive cloud management portals:
- Nile Control Center (for IT Admins): A centralized portal for managing network services, monitoring applications, users, and devices, and enforcing security policies.
- MyNile (for End Users): A self-service portal that allows users to monitor device performance, check network outage status, identify application issues, view health metrics, and run performance tests. If problems occur, users can quickly open trouble tickets from the portal, streamlining IT support.
In addition to Nile’s continuous AI-powered network monitoring, these portals help IT teams manage operations efficiently while equipping users with tools to resolve common issues on their own.
Industry Architecture Comparisons: How Nile Stands Apart
When compared to traditional enterprise networking and other cloud-managed architecture offerings, Nile offers several distinct advantages:
| Feature | Traditional Networking | Cloud-Managed Networking | Nile Access Service |
| Deployment Model | Hardware-centric, manual task oriented | Cloud-controlled but hardware-dependent | Fully cloud-native with AI-driven assistance |
| Security | Perimeter-based, vulnerable to lateral movement | Limited Zero Trust enforcement requiring add-on tools | Fully-integrated Zero Trust security from Infrastructure to Policy Layer |
| Automation | Minimal, with insights that require heavy manual interaction due to architecture unpredictability | Expanded insights due to cloud data lake advantage, but still limited due to architecture unpredictability | AI-driven closed-loop automation based on a standardized architecture |
| Operational Simplicity | High complexity, with repetitive manual management tasks | Simplified UI but with complex manual setup and configuration | Simplified operations that eliminate VLANs, QoS, and ACLs, etc. |
Nile’s approach removes complexity, reduces costs, and enhances security by combining automation, cloud orchestration, and AI-driven intelligence—delivering a network that operates with unprecedented efficiency, resilience, and adaptability.
Conclusion: Redefining the Future of Networking
Nile’s Modern Campus NaaS redefines enterprise networking by integrating a modern cloud architecture, AI Automation, and built-in Zero Trust security. Organizations that have adopted Nile’s architecture have benefited from a more agile, cost-effective, and resilient network infrastructure.
For organizations seeking to radically eliminate complexity, enhance security, and reduce costs, the Nile Access Service presents a transformative networking solution that meets the demands of today’s hybrid work, IoT-heavy, and fast-paced digital era.