Share Via
Capture the Flag Challenge results in zero breaches
With 100+ security professionals ready to break into our Zero Trust Fabric, they launched more than 1 million attacks and probesfrom tools like Nmap, Nessus, and Metasploit. The results were pretty telling. Native per-device isolation and Layer 3 segmentation did exactly what it was intended to do, turning away every single attack.
What made this interesting was not just the numbers, but how Zero Trust principles and a network should perform in the real world. These were not theoretical attacks or simulations. These were skilled hackers throwing everything they had at a live network. The fact that traditional lateral movement techniques failed to expose data or reach a neighboring device demonstrates why Nile customers are moving away from flat networks and VLAN-based setups. Not to mention the complexity, cost, and failed Zero Trust and micro- segmentation projects they’re experiencing.
What Makes the Nile Zero Trust Architecture Different
Most Capture the Flag testbeds are built on traditional network architectures that bear little resemblance to real-world enterprise deployments. Vendors spend weeks or even months locking down every possible port, gateway, firewall, and VLAN imaginable. Target machines quietly await a predictable set of exploit attempts. It is amusing, but nothing like the messy, fragmented networks IT and red teams face in the real world.
Instead of a heavily staged, unrealistically test environment, hackers stepped up to a fully isolated, Zero Trust enterprise LAN designed to block threats by default—without any custom fine-tuning. Every endpoint is placed into a segment of one, and each traffic flow is individually enforced. Lateral movement only happens if firewalls are misconfigured—and even then, you may not get as far as you would expect.
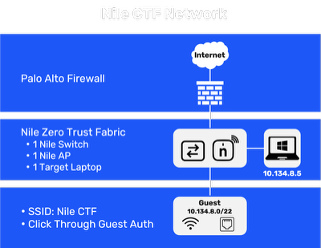
We kept the setup intentionally simple. The Nile network consisted of the following components:
- 1 – Purpose-built Nile Zero Trust Fabric AP
- 1 – Purpose-built Nile Zero Trust Fabric switch
- 1 – Windows 11 laptop set up as a target device
- 1 – Firewall for Internet connectivity
There are no VLANs to exploit, no broadcast domains to sniff, and no lazy Layer 2 design. If your existing lateral movement strategy relies on a flat network or on NAC appliances and complex add-ons, consider this a wakeup call.
The Challenge
We invited hackers to connect to either the wired or wireless network, which shared the same subnet as the target device. After connecting, the first task was to identify the device’s MAC address. From there, participants needed to access a .txt file on a file share and gather information from a running SQL server.
On a traditional network, this would be a beginner-level exercise.
Phase 1: Discovery. More Importantly, The Lack of Discovery
In a flat Layer 2 network, discovering other devices is straightforward. ARP requests broadcast across the subnet, ping sweeps reveal live hosts, and network scanners quickly enumerate everything on the wire. Participants expected to have the target’s MAC address within seconds.
Because Nile’s per-device Layer 3 isolation puts every endpoint into its own segment-of-one, there are no broadcast domains to leverage, so traditional discovery techniques that rely on Layer 2 adjacency simply do not work. Instead, ARP requests stay contained within each isolated segment, never reaching other devices on the network.
Conventional discovery techniques failed to reveal the target device. Unlike traditional networks that rely on extensive and error-prone ACLs, Nile’s Zero Trust Fabric is architected to eliminate this reconnaissance path altogether.
Phase 2: Lateral Movement Mitigation
Even when the hackers knew the target’s IP address (which we made public), the real challenge began: establishing a connection to download a file or connect to the SQL Server.
In traditional networks, once an IP address is known, you can probe for vulnerabilities or exploit misconfigurations in network segmentation. Attackers typically attempt SMB exploitation, RDP brute forcing, or using tools like Metasploit to reach unpatched systems. VLANs in the old model provide some separation but often have routing between them. NAC solutions authenticate at connection time but do not continuously enforce per-flow isolation.
In contrast, Nile’s architecture is fundamentally different. Every traffic flow between endpoints requires explicit authorization. When attempting to connect to the SQL server or access file shares, those packets never reached the destination. The Zero Trust Fabric blocked the traffic as a policy; permitting device-to-device communication did not exist. At this point, participants realized this was not a typical challenge.
Why Build a Capture the Flag This Real?
Unlike most hackathons, we didn’t build a testbed. Every Nile deployment is based on a standardized Zero Trust Fabric that delivers enterprise-class security on day one. No complex add-ons. No legacy principles with well-known vulnerabilities that hackers see as your weakest links.
By exposing our standardized architecture to hackers, we gave them a rare opportunity to attack something real that anyone can subscribe to and deploy. A network that they can learn from and how Nile’s modern Zero Trust and segmentation model disrupts lateral movement, which principles are now preferred, and which ones belong in history books.
This was a hands-on look at why the tradition of building VLAN-based networks is over—and why modern Zero Trust principles matter.
Curious how this applies to your organization’s security challenges? The same architecture that stopped every attack at Deadwood can protect your enterprise. Reach out to us at Nile to discuss how a modern Network-as-a-Service (NaaS) architecture with built-in Zero Trust Fabric can transform your security and compliance strategy for the long haul.