Share Via
In a previous blog post, I outlined the expectations, value, and some concerns that we encounter when discussing wireless guest access with customers. While organizations will provide guest access to their visitors as a convenience, today’s offerings lack basic security features as the connecting devices are not under the control of the organization’s IT department. You’re basically dealing with a separate SSID and VLAN for segmentation purposes, which is not the most ideal security scenario.
VLANs place everyone’s devices onto a shared segment that allows for lateral movement, VLAN hopping, snooping, and worse. To eliminate the shared nature of a VLAN we built a more granular segmentation model into our Nile Access Service as a starting point. Anyone using a Nile network that connects to a guest SSID, or the internal network for that matter, is placed into a segment of one for isolation and enhanced security.
With secure guest access in mind, we also offer the Nile Guest Service, which is an add-on option that takes advantage of our per-device isolation and completely separates how guest traffic is handled. In essence, you can treat guest access and its management similar to the offload of having payroll taken care of by a trusted third-party. In the guest scenario, you simplify the process by eliminating complex on-premises infrastructure configuration and dedicated NAC guest solutions and forward all traffic to a local Nile cloud instance for handling.
The clear advantage is a guest access network that is very secure, does not require a large amount of setup and offers cloud flexibility and management assistance. The image below shows you a high-level picture of how the Nile Guest Service stacks up architecturally versus the traditional guest service from other vendors.
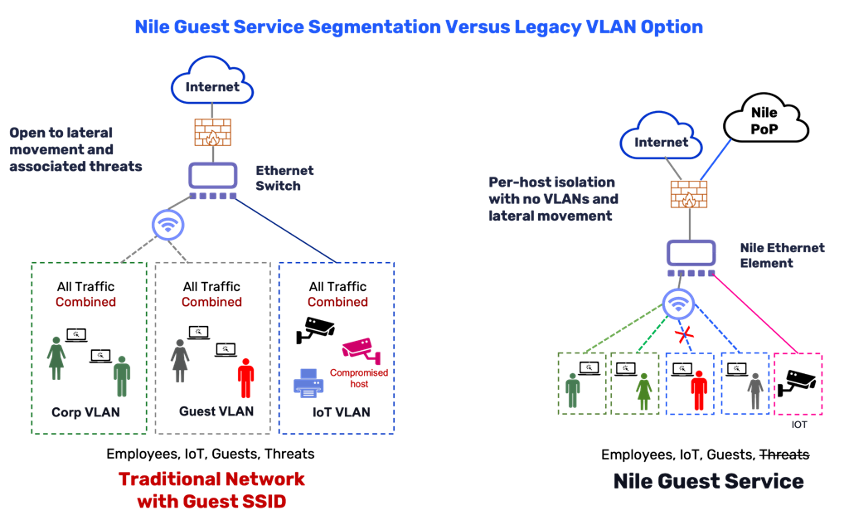
Here’s a brief summary of how the Nile PoP Guest Service works:
- Setup and Configuration: Wireless solutions typically require setting up a guest access SSID to allow device connections, and most of these guest networks need a passcode for access. That’s where the Nile Guest Service is different. IT teams no longer need to configure on-premises firewalls, access control lists, and NAC solutions to separate guest traffic for every location.
- All traffic is tunneled or sent to a local Nile cloud point of presence (or PoP) for inspection and distribution to its destination – the Internet or elsewhere.
- DHCP addressing: The Nile Guest Service add-on includes the use of the Nile’s DHCP Service which eliminates dedicating IP addresses for visitor use. An address used for guest devices comes from a pool of Nile hosted addresses for security and convenience.
- Segmentation and Data Protection: Because each device connects to our standardized per-device isolation and Layer 3 segmentation architecture, there are no VLANs and lateral movement initiated threats, like VLAN hopping or snooping, which is inherent to lateral movement within a VLAN. Due to the direct forwarding of guest traffic to the Nile cloud instance, your guest and internal networks are inherently more secure.
- URL Filtering: As organizations are responsible for the actions of their guests, it’s simple to set up URL filtering rules that deny access to adult, gambling, and other unwanted sites. A layered approach to filtering provides flexibility in which categories of sites are blocked. For instance, if filtering on social media sites, you can specifically permit access to YouTube while blocking all other social media sites..
- Digital Media Misuse: An additional advantage is that Nile works with authorities on behalf of our customers for any Digital Millennium Copyright Act (DMCA) issues as part of the service. DMCA is designed to protect artists and content owners If someone is using, making or distributing unauthorized copies of copyrighted material. which is a federal law and includes severe civil or criminal penalties if/when caught.
Conclusion
In this day and age where users are very familiar with an Internet Cafe or Coffee Shop style of connecting to a guest network, you now have the ability to provide them with a secure option in an office, store or other public venue. We’ve also removed VLANs, complex configuration steps, special authentication supplicants required on guest’s devices, and the management headaches. The choice is a new campus Zero Trust network versus using a traditional architecture that a bad actor understands is a weak link and can exploit.
Best of all, no matter which Nile guest access option you choose, we work with you to ensure that your internal network and resources, as well as your guest’s devices and personal data meet today’s increasingly stringent security and compliance requirements. No excuses.
For reference:
Feel free to contact us here with any questions or comments.