Share Via
Networks – providing for collaboration and application access – are the cornerstone of any business today. Securing these networks from cyber security threats is increasingly complex. It’s arguably never been more challenging to deliver a secure enterprise network. This makes the recent integration announcement of NaaS by Nile with Palo Alto Networks Next-Generation Firewalls (NGFWs) a timely one.
The integration delivers a secure end-to-end networking architecture for enterprise campus networks. Until today, NaaS by Nile partnered with Palo Alto Networks’s NGFW extended zero trust into the campus network, securing access and transport while eliminating the possibility of malware proliferation. Now, the latest integration additionally opens increased visibility and granularity for centralized policy enforcement.
Getting Granular
This collaboration is a major security win for our customers. Getting granular is about extended visibility and deeper policy enforcement. By leveraging Palo Alto Networks’ API integration, we’re now able to offer increased visibility into policy enforcement. This approach provides deeper visibility into E/W/N/S network traffic by having Palo Alto Networks’ firewall leverage insights from Nile for policy enforcement. Beyond simply relying on IP addresses, the addition of user and group information provides more context for fine-grained policy that is highly specific and precise, allowing for more granular control and security.
Here we see how Palo Alto Networks’ dashboard has more visibility and context beyond a blind, numerical IP address. We see each IP address associated with a user ID and also the group-tag they belong to. This adds additional context to the actions taken by Palo Alto Networks’ NGFW.
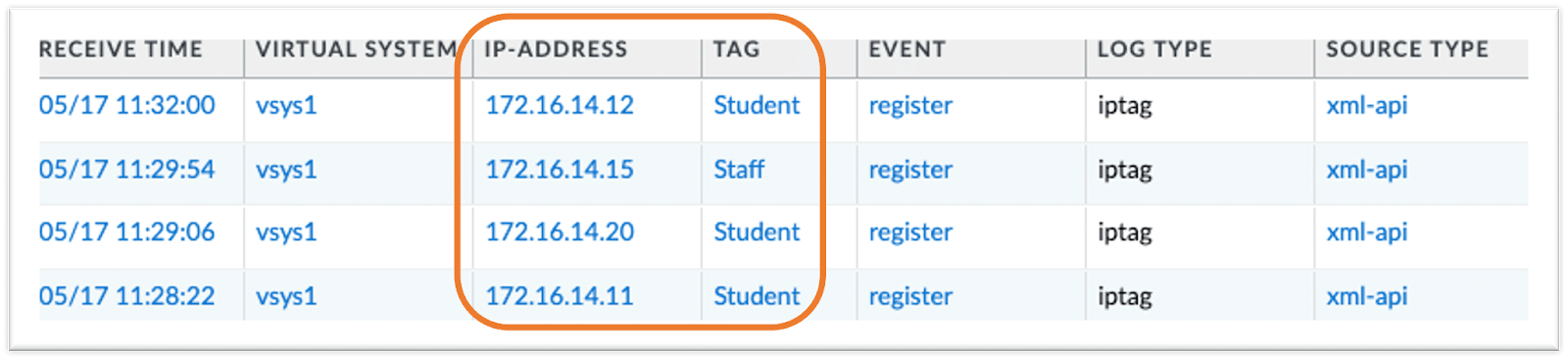
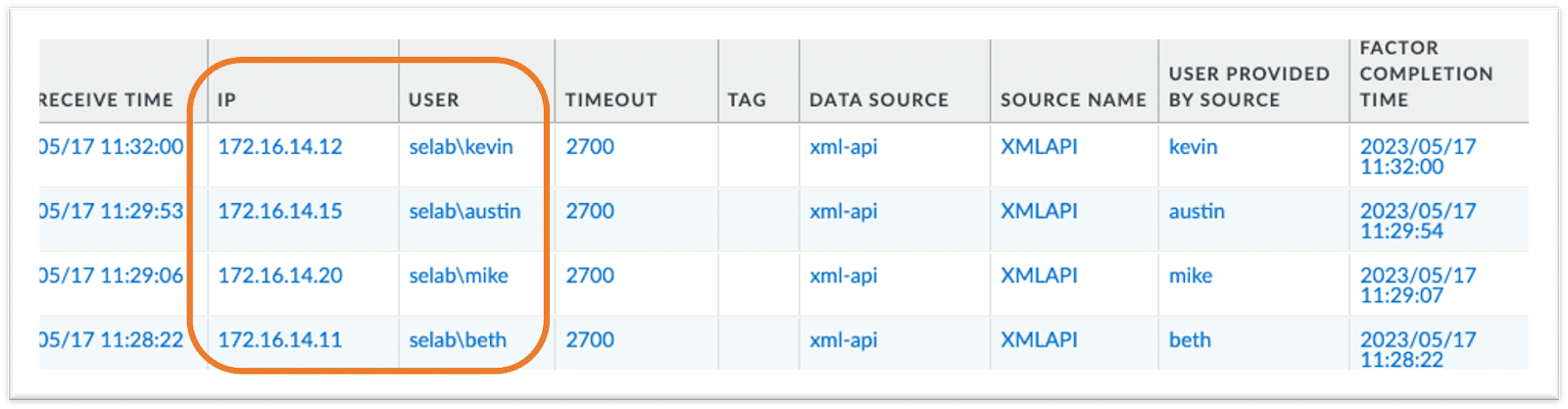
Adding user and group context to numerical IP Address
Not all users are equal. There are always exceptions. Maybe all students shouldn’t have access to certain applications, but a research student with special approval can (see real-life example below). With the new Nile/Palo Alto Networks integration, policy can also be enforced beyond the group level and into the user level, providing more granular policy capabilities when needed.
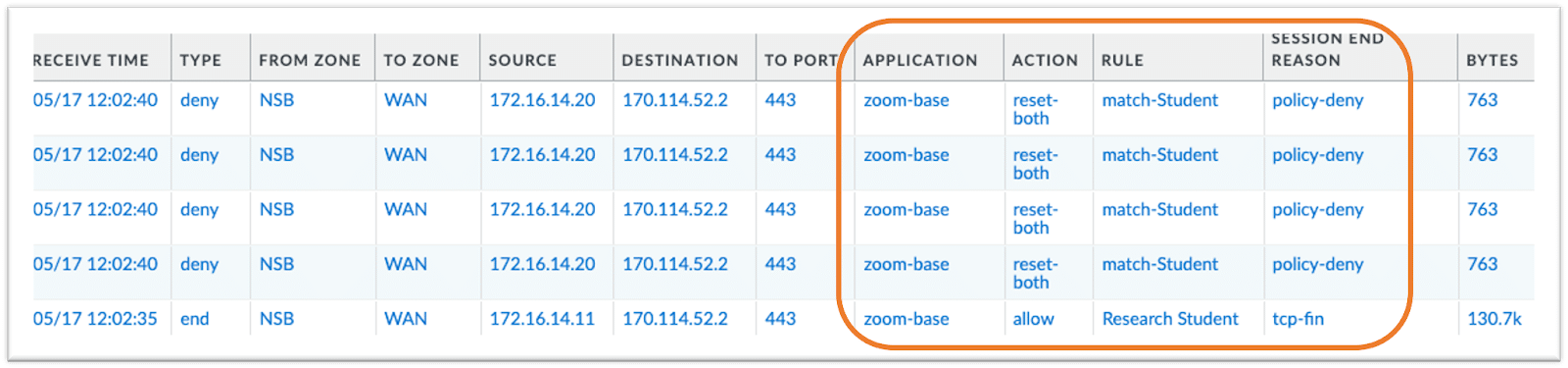
Applying granular user-exception rules within a group-tag
Extending Zero Trust Into the Campus Network
The LAN requires multiple layers of security, from authenticating and authorizing user/device access to securing network traffic to securing the actual network infrastructure itself. It is a system of layers of legacy protocols, each requiring configurations, that all must somehow thread together and do its basic function: secure access. And yet, it is maddeningly complex.
This is where the Nile/Palo Alto Networks integration comes in.
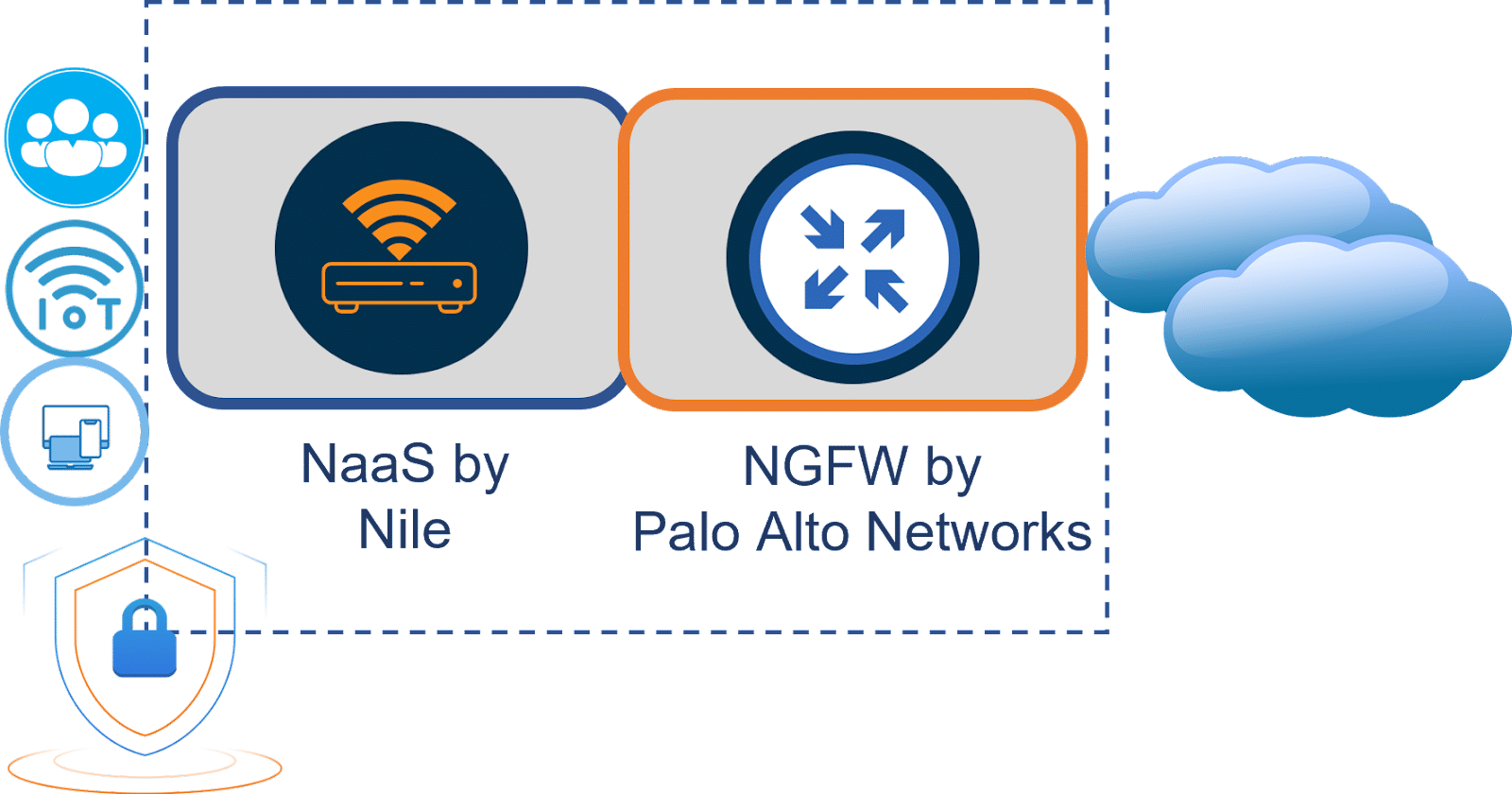
Let’s talk about securing access and the network itself. Built upon the principles of zero trust, Nile authenticates every user and device using multiple methodologies, i.e. IEEE 802.1X across wired and wireless. Beyond user and device access, Nile delivers end-to-end network traffic encryption by default; there is no extra SKU or add-on. As traffic journeys thru the network elements, we are assured that every element is secure and authorized in itself with TPM-certificate authentications.

Nile is engineered from a clean slate, shedding the burden of legacy protocols. NaaS by Nile prohibits peer-to-peer communication by employing host-based segmentation delivered through zero trust isolation.
All network traffic is forwarded to Palo Alto Networks NGFW where traffic is inspected, potential malware can be detected and is blocked from proliferating throughout the network. This combination of host-traffic isolation and centralized firewall policy enforcement stops malware proliferation cold and simplifies workflows. All this is done with zero configurations. Every host device, even down to the smallest IoT – and generally most vulnerable – device on the network is fully protected.
The combination of NaaS by Nile and Palo Alto Networks’ NGFW creates a powerful force with which to secure the enterprise network, access, and traffic.
Watch the demo!
Read our press release.
See the interoperability brief and the integration guide.
Share Via



